The Real Fascist is His Fraudulency Joe Biden*
*Or whoever has his hand rammed up that meat puppet’s ass.
Brandon (which I will use as a term for whoever is the power behind the Porcelain Throne) has thrown down the gauntlet…but in a way where most of America will never see it. The networks didn’t carry his tirade. CNN air brushed it (or whatever you call editing the red background) for its five viewers (who aren’t trapped in airports).
Luckily for me I live in Colorado, and therefore, despite my best efforts, I probably didn’t vote for Donald Trump.
Of course, for this purpose who I actually did try to vote for will be essential, and they undoubtedly know.
Come and get us, asswipes!
https://www.youtube.com/watch?v=3h6ZZ28QtX4
Justice Must Be Done.
The prior election must be acknowledged as fraudulent, and steps must be taken to prosecute the fraudsters and restore integrity to the system.
Nothing else matters at this point. Talking about trying again in 2022 or 2024 is hopeless otherwise. Which is not to say one must never talk about this, but rather that one must account for this in ones planning; if fixing the fraud is not part of the plan, you have no plan.
Small Government?
Many times conservatives (real and fake) speak of “small government” being the goal.
This sounds good, and mostly is good, but it misses the essential point. The important thing here isn’t the size, but rather the purpose, of government. We could have a cheap, small tyranny. After all our government spends most of its revenue on payments to individuals and foreign aid, neither of which is part of the tyrannical apparatus trying to keep us locked down and censored. What parts of the government would be necessary for a tyranny? It’d be a lot smaller than what we have now. We could shrink the government and nevertheless find it more tyrannical than it is today.
No, what we want is a limited government, limited not in size, but rather in scope. Limited, that is, in what it’s allowed to do. Under current circumstances, such a government would also be much smaller, but that’s a side effect. If we were in a World War II sort of war, an existential fight against nasty dictatorships on the brink of world conquest, that would be very expensive and would require a gargantuan government, but that would be what the government should be doing. That would be a large, but still limited government, since it’d be working to protect our rights.
World War II would have been the wrong time to squawk about “small government,” but it wasn’t (and never is) a bad time to demand limited government. Today would be a better time to ask for a small government–at least the job it should be doing is small today–but it misses the essential point; we want government to not do certain things. Many of those things we don’t want it doing are expensive but many of them are quite eminently doable by a smaller government than the one we have today. Small, but still exceeding proper limits.
So be careful what you ask for. You might get it and find you asked for the wrong thing.
Political Science In Summation
It’s really just a matter of people who can’t be happy unless they control others…versus those who want to be left alone. The oldest conflict within mankind. Government is necessary, but government attracts the assholes (a highly technical term for the control freaks).
A Few Things We Cannot Blame on His Fraudulency
I am pretty sure Joe Biden had nothing whatsoever to do with the 30 Years War that ran from 1618-1648 and probably killed about a third of the people then living in what is now Germany.
Nor did he cause the collapse of either Roman empire (Western, 476 CE, Eastern 1453 CE). Nor the ignominious failure of most of the Crusades. Nor the collapse of Bronze Age civilization around 1200 BCE (including the collapse of the Minoans and the blowup of Santorini).
However, my utter lack of ability to imagine how he could possibly be responsible for these things is not a valid argument against them, so I await correction if appropriate.
His Truth?
Again we saw an instance of “It might be true for Billy, but it’s not true for Bob” logic this week.
I hear this often, and it’s usually harmless. As when it’s describing differing circumstances, not different facts. “Housing is unaffordable” can be true for one person, but not for another who makes ten times as much.
But sometimes the speaker means it literally. Something like 2+2=4 is asserted to be true for Billy but not for Bob. (And when it’s literal, it’s usually Bob saying it.) And in that sense, it’s nonsense, dangerous nonsense. There is ONE reality, and it exists independent of our desires and our perceptions. It would go on existing if we weren’t here. We exist in it. It does not exist in our heads. It’s not a personal construct, and it isn’t a social construct. If there were no society, reality would continue to be what it is, it wouldn’t vanish…which it would have to do, if it were a social construct.
Now what can change from person to person is the perception of reality. We see that all the time. And people will, of course, act on those perceptions. They will vote for Trump (or try to) if their perception is close to mine, and vote against Trump (and certainly succeed at doing so) if their perception is distant from mine (and therefore, if I do say so, wrong). I have heard people say “perception is reality” and usually, that’s what they’re trying to say–your perception of reality is, as far as you know, an accurate representation of reality, or you’d change it.
But I really wish they’d say it differently. And sometimes, to get back to Billy and Bob, the person who says they have different truths is really saying they have different perceptions of reality–different worldviews. I can’t argue with the latter. But I sure wish they’d say it better. That way I’d know that someone who blabbers about two different truths is delusional and not worth my time, at least not until he passes kindergarten-level metaphysics on his umpteenth attempt.
Lawyer Appeasement Section
OK now for the fine print.
This is the WQTH Daily Thread. You know the drill. There’s no Poltical correctness, but civility is a requirement. There are Important Guidelines, here, with an addendum on 20191110.
We have a new board – called The U Tree – where people can take each other to the woodshed without fear of censorship or moderation.
And remember Wheatie’s Rules:
1. No food fights
2. No running with scissors.
3. If you bring snacks, bring enough for everyone.
4. Zeroth rule of gun safety: Don’t let the government get your guns.
5. Rule one of gun safety: The gun is always loaded.
5a. If you actually want the gun to be loaded, like because you’re checking out a bump in the night, then it’s empty.
6. Rule two of gun safety: Never point the gun at anything you’re not willing to destroy.
7. Rule three: Keep your finger off the trigger until ready to fire.
8. Rule the fourth: Be sure of your target and what is behind it.
(Hmm a few extras seem to have crept in.)
(Paper) Spot Prices
Last week:
Gold $1,794.00
Silver $23.31
Platinum $999.00
Palladium $1,780.00
Rhodium $12,800.00
This week, 3PM Mountain Time, markets have closed for the weekend.
Gold $1,799.50
Silver $23.82
Platinum $1,033.00
Palladium $1,832.00
Rhodium $12,750.00
Gold was well over $1800 earlier this week, and looked to be solidifying its position there, so of course it had to be shoved back down. (Uppity PMs!) It might at some point in the very near future, become more valuable than palladium. (Which still seems absurdly overpriced to me; I can remember when it was less than midway between silver and gold.)
Qubes OS In Some More Detail
A few months ago I mentioned Qubes OS. (https://www.qubes-os.org/. The intro page covers a lot of what I’m saying in someone else’s much more carefully crafted words; I could probably do as well if I wanted to spend weeks writing instead of two days: https://www.qubes-os.org/intro/ .)
Qubes bills itself as a “Reasonably Secure Operating System.” Yes, that doesn’t sound super duper confident, but security, be it physical or in cyberspace, is inherently imperfect. Your adversary…be it some shitbag who wants your credit card number or to hit you with a ransomware attack, some other shitbag in a fancy building with a cute logo that wants to saturate you with inane “targeted” advertising so he needs to know how many squares of toilet paper you use, or a Deep State actor who’s unhappy because you understand what kinds of shitbags are running this country (I guess “shitbag” is the common denominator) gets a say in how good your security is–by doing his best to make sure it’s not good enough.
What Qubes helps you do is to implement some fairly basic principles of security, that most computers are absolutely miserable at doing. (So miserable, one would think it was deliberately bad in some cases…I am looking at YOU, Micro$haft.)
The main benefit to Qubes is compartmentalization. If you want to both a) do online banking (which means you have a glowing red target painted on your hindquarters) and b) go to some of the, shall we say, dodgier areas of the internet (and no, that’s not necessarily porn sites), then what you’re begging for is to have some guy who’s giving you that stuff for “free” decide he wants payment with your bank account, and he will try to collect without your knowledge or consent. Even sites that aren’t trying to be dodgy might have ads on them that mask a hacker trying to get into your system. And sometimes they do that by tricking you into clicking on a link. Yes, we can be our own worst enemy.
What’s the best way to ensure the scumbag doesn’t get your online banking password? Or your credit card number? By not having it be on that computer in the first place! That way he can’t rape you online and you can’t accidentally help him rape you online.
Cthulhu has often mentioned that he has multiple different physical computers, each having a specific purpose. (I have visions of a house cluttered with little Raspberry Pis everywhere; sit on the couch and the cushion is lumpy because there’s a computer under the cushions, right next to the 68 cents in change he lost two weeks ago.)
You can go that far, but then there will be times you do have to move data from one machine to another and that’s a solid pain the ass. I know this because I was doing something similar.
Compartmentalizing with Virtual Machines
The second best (and sometimes arguably better anyway) method to go is with virtual machines. That’s a setup where there are two (or more) software systems on the same physical computer that are both like “brains in a vat”. Each one sees itself as a computer; they’re really two or more different programs running on the same computer. Of course there’s a system running on the box that really is in control, and it’s providing little “bubbles” for the virtual machines to live in. So you can have one virtual machine that you use, say, to visit here, and a totally different one to use to do online banking. Each is unaware of the other’s existence. And–most importantly–many of these virtual machines can be running at the same time. (It’s expensive; you need a fairly powerful processor and lots of RAM memory to do it.)
What you can’t do, however is keep the “controlling” system from knowing what’s going on. It’s the controller, it has to know something about the other machines just to do its job.
Qubes uses virtual machines for everything, and I mean everything.
There are at least two ways to “do” virtual machines.
One is to install a virtual machine application on an otherwise normal system, called the “host” system. The host actually has direct contact with your hardware–keyboard, mouse, monitors, network connections, usb thumb drives, sound card…et-nearly-endless-cetera. The virtual machine app runs inside that operating system, and it creates and manages the virtual machines, letting you start them and stop them, and arranging for limited communications between them. It also lets those machines “talk” to your computer hardware, though it may do some sleight of hand in there…for example, you open a window with Virtual Machine A in it, and the controller tricks Virtual Machine A into thinking that window is your entire video driver. If that window is 1200×800 pixels, Virtual Machine A thinks you have one 1200×800 pixel monitor. Another window has Virtual Machine B in it, and that system thinks that other window is the monitor. This is the method used by Oracle VirtualBox, and that is the software I used to use.
The problem with this is you still have a regular machine that can be readily hacked because it’s directly connected to the internet, and the virtual machine app depends on it. In other words, the controlling system, a big bloated OS with lots of ways to be attacked, is directly exposed, and once a hacker has it, it’s game over.
The other method of doing virtual machines is to run the virtual machine controller directly on your hardware. And since it does nothing but fire up virtual machines and connect hardware to different machines, it’s a bit harder to attack. Also it can be expressly designed to manage your hardware without actually connecting to it (and giving hackers a possible doorway into it). It’s the difference between plugging something else in, versus sticking your own fingers into the electrical socket.
Qubes chose the latter method, using something called the Xen Hypervisor. When your system boots, it boots directly into Xen Hypervisor, not Micro$haft Windows, not Linux, not MacOS, not Android.
Xen Hypervisors starts up a special virtual machine called dom0 (domain zero). This will be the controller. But the controller doesn’t necessarily have primary access to your hardware. It does not get access to your network cards, for instance, so it is isolated from the hackers. It also usually doesn’t get access to your USB ports but an exception is made if you have a USB keyboard or mouse. (Some older machines still have the special PS-1 plug for those.) Having USB be separated is a good thing, because USB is used for a lot of sneaky attacks like the thumbdrive “accidentally” dropped in a parking lot that is full of malware for the first careless geek who says, “Hmm, I wonder what’s on this?” (Cthulhu explained below that the USB protocol allows a device to ‘set your system up’ without asking permission, and that’s why USB is so noxious from a security standpoint.)
Dom0 is used to start and stop other virtual machines, and is also used as an intermediary for those situations where one VM must talk to another.
(And those situations do arise. Another aspect of the way Qubes does things is that NO such communication happens without your specific approval. Want to move a file? You can do it, but you will be prompted to select which VM it’s going to and press OK. If that prompt ever shows up out of the blue (and not because you wanted it to), then alarm bells should ring in your skull and you should definitely hit cancel, not OK. This popup will show up if you’re using GUI menus to copy the file, or if you do it from the command line. (Command line versions of commands usually don’t show on the GUI so hackers love them.) A similar process happens with copy-and-paste, which, between VMs, is a four step process, not a two step one.)
In addition to dom0 you have a VM whose sole job it is to manage your network; that one is called sys-net. It is given direct access to your network card(s). And another one which implements a firewall, sys-firewall. Your system connects sys-firewall to sys-net, then it connects whatever VM(s) you use to talk to the internet, to sys-firewall. The actual firewall rules are on that last VM, so you can create one for online banking that only lets you connect to the bank website, and another one that’s more wide open for surfing the web.
And yes, you as the user are free to create as many VMs as you want. When you first install Qubes it comes with VMs named “Work,” “Personal” and “Vault.” This gives you a way to keep your job separate from your personal stuff, right off the bat. But let’s say you have five or six clients–you can create a separate VM for each of them! No risk of sending the wrong thing to the wrong client. Or maybe you’re writing software and have two totally different projects in different languages going on…split them up!
Vault is “special” because it has no network connections at all. It’s a place to store passwords. Those get VM-to-VM copied and pasted into the VM that’s on the network. So a hacker who’s gotten control of that VM can only get that password; they don’t get your list of passwords (which is not only not on that VM, but is kept in an encrypted database anyway).
You can also choose what runs on the virtual machines. Dom0 will run Fedora Linux (no choice there), but your VMs can run Debian Linux (similar to Ubuntu), Windows 7, 10, or 11. Or something called whonix, which is set up to let you browse the web anonymously, through VPNs that can literally pop up all over the world. It’s really hard for black hats to trace. There are other third-party supported versions of Linux out there, too; even though they are third party the Qubes site has links to them.
[And yes, you can safely run Windows 7…provided you never hook it up to the internet. And you don’t have to. (But this does mean you can’t use it for surfing the internet.) There’s even a third party Windows XP setup out there. And you can safely run Windows 10 and 11…safely in a different sense, in that you can keep them from phoning home and telling Asshole Gates what you are doing, by never connecting them to the network.]
At this level there’s one other feature; you can color-code your VMs. They will open up in windows with different colored frames as another visual cue that they are different VMs. However, there are exactly eight colors, and it’s easy to end up with more than eight VMs (I have a couple of dozen). Generally dom0 and the system VMs and templates (I’ll explain “template” in a moment) are black, with user-type qubes (the ones you actually do things on) being red, orange, yellow, green, blue, purple or gray. Different people have different color codings.
OK, so keeping things separated from one another helps in case you do get hacked, but what does it do to help keep you from getting hacked in the first place?
To be honest, not much more than any other system. In fact, they assume you will get hacked. But it can help you remove the hack quickly, which is nearly as good. Consider, someone sends you an infected attachment in e-mail. If you open your attachments in a different VM, then when you open that infected attachment, you can simply throw away the VM it infected. In fact, you should do this whether or not you think the attachment might be infected, just in case. Since you were never planning to use that VM for anything else ever again anyway, you’ve lost nothing by throwing it away…except an infected system.
Digging deeper into Virtual Machines.
I mentioned “templates” before, and now I’m going to explain that. Qubes does VMs a bit differently from most systems.
Have you ever wondered, in exasperation, why the heck the part of your computer that contains the operating system can’t just be made read only so viruses can’t infect it? Well, you can get close to that with Qubes. It has a way of separating the operating system and applications areas from your personal files.
There are two main types of VMs in Qubes…TemplateVMs and AppVms. (That last name is not the best name they could have come up with; it can be a bit misleading as you’ll see soon.)
A TemplateVM is for installing software on. Installing only. You do that the standard way for Linux with apt or dnf commands. To do this, you have to log in to that VM, but you don’t do anything on the Template. The template in other words is a “clean” install of your applications onto a clean install of the operating system. Yes, there’s a “home” area for user accounts and you just used it while you were installing stuff, but you didn’t change anything there…and if you did it won’t matter anyway. NEVER connect a TemplateVM to sys-firewall or sys-net, even if you’re putting a browser on it. (The installation process follows some other route I frankly don’t understand, to get the software off the internet to install it–probably one with lots of intermediaries.)
When you create an AppVM, you must base it on a TemplateVM. (Interestingly, later on you can change it, but that can sort of pull the rug out from under you.) So let’s say you created a template with Brave Browser on it, :brave-template.” You can create an AppVM and name it “theqtree” and base it on brave-template.
When you start theqtree, you have a virtual machine with Brave installed on it. (But before you do that, connect it to sys-firewall.) You can save bookmarks, download files, set up Brave how you like it, and that will all be remembered from one startup of theqtree to another. BUT if you visit a web page that tries to install malware in the system area, that malware will not be there the next time you start theqtree. (That is not immunity from malware installed in your user area, though.)
How does that work? Well when you start theqtree, you get your user area, like it was when you shut theqtree down last time. But for a program area, you get a copy of the one from the template. And this copy does not get saved when you shut theqtree down. So something that gets installed there, or even changes to a system configuration file, will go away when you shut theqtree down. But the files you downloaded (to your Downloads folder) are in your user area, so they are not lost. Your bookmarks and so on are also there. And likely, it will even remember your open tabs. (It’s easy to forget this and make a deliberate change to the system/apps area, and lose the change when you shut down.)
So that’s one quick way to recover from a virus…shut it down and restart it. If the virus is in the system area, it’s gone.
It’s possible to base multiple AppVMs on one template, so you can create a different AppVM, using the same Brave template. So you can keep your online banking and your conspiracy theories separate!
BUT if something gets into your user area instead of your system area, you’re stuck with it, until you throw away the AppVM.
(By the way, the VMs I mentioned before, sys-net, sys-firewall, work, vault, personal…are all AppVMs. As distributed, they are all based on the same template, which will either be a vanilla install of debian or fedora linux, with a lot of different apps preinstalled. That means that firefox, which is installed by default, exists in your vault VM, uselessly since from there it can’t connect to the internet; sys-net, conversely, has no need for keepass (a password manager), but every VM has it. There are ways to fix this, but they’re for more advanced users.)
I think we’re finally ready for a picture…I’d have showed it earlier, but too much of it was unexplained before now.
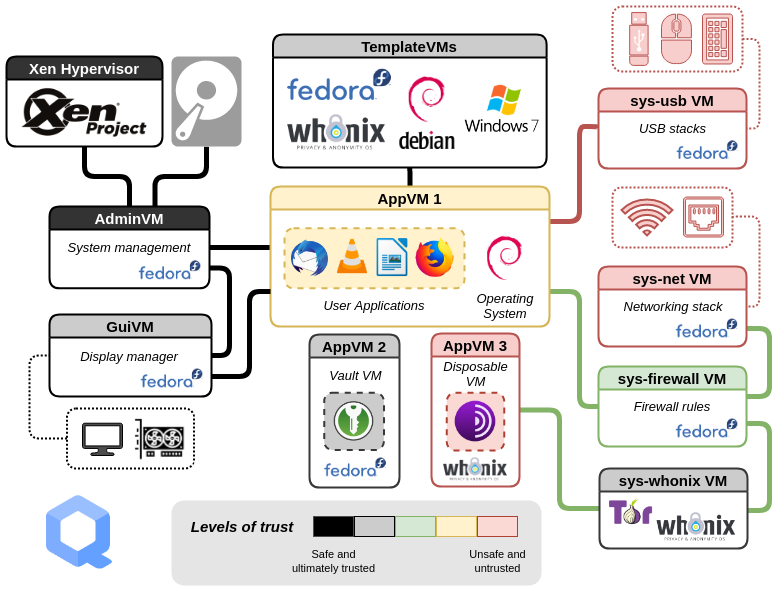
Disposable Virtual Machines
Now there’s another level of complication that can help with ANY malware infection, even one in your user area. Notice that in the diagram above that AppVM 3 is labeled “disposable VM.” What does that mean?
A disposable VM is one that self-destructs as soon as you close it. It’s based on a template, too, but the template is an AppVM, not a templateVM. (This causes a lot of confusion.) Basically the disposable makes copies of the AppVM’s user area, and the system area of the template VM the AppVM is based off of, and those disappear when it shuts down, just like the system area of the AppVM closes when you shut down the AppVM.
A disposable is really handy for looking at attachments sent with an E-mail, too. If it’s some dodgy thing Pgroup sent you, and it infects your disposable, so what? The infection is sterilized the instant you close the window on the disposable.
The advantage to having the disposable be based on an AppVM is that you can (for example) get Brave set up just the way you like it in an AppVM, but not actually visit any sites. Then set up the AppVM to act as a disposable template, and whenever you go to a site you don’t trust, use a disposable. When the disposable opens, you have a fresh copy of Brave (but set up how you like it); you go to that dodgy site pgroup.com, then close the browser window and POOF!!! that machine no longer exists.
There are two slightly different flavors of disposables, named disposables and ones that aren’t named. A named disposable has to be explicitly shut down, the other ones will get a random number name like disp37 or disp7734, and they tend to pop up when you’re looking at an email attachment or the like. That attachment will open in say LibreOffice (which can read Micro$haft Word files), but when you close the LibreOffice window, the VM shuts down. But if you were to open a named disposable, such as LibreOffice-Disposable, you have to remember to shut it down afterwards. (I came up with a trick to avoid that, by the way.) Otherwise, they’re the same: they both go POOF when they shut down–it’s just that one of them makes sure you don’t forget to shut it down. I make heavy use of both kinds.
So why did I decide to write this now? Well, I have actually customized the hell out of my install and it’s finally looking like I want it to–which as it turns out is not a whole lot like that diagram (there’s a lot of stuff I’m doing which I didn’t even mention). So this is by way of celebrating that.
A Case Study: The Great Notifier Kerfuffle
But also because I was reminded about all of this when, last week, we had that big kerfuffle over the way Wordpus broke the notifier. And I found myself really appreciating Qubes when Wolf and I were trying to debug my broken notifier.
I have a template that has nothing but an absolutely bone-stock Firefox ESR install on it. I didn’t have any AppVMs based on it, it was what I call an “intermediate” template. Because I often create templates by cloning other templates, then adding more stuff to the clone. In this case I cloned the bone-stock firefox and, then on the new template, I customized the heck out of FIrefox. (Firefox has ways to customize it in the installation/system area, which is how companies with 60,000 employees can set up FIrefox the same annoying way for all of their employees and even block them from customizing it themselves–they have a customized Firefox installation package with all of the options preset they way they want to inflict on you. I actually set up Firefox that way, myself, so the customizations are actually in my cloned template, not in my user area. Most software does not work that way.)
I was using an AppVM based on the customized template, to browse QTree that day. Why an AppVM? So it would keep the cookies that tell wordpress and QTree that I am logged in. Yes, I risk getting infected and keeping the infection, but when QTree logs me out anyway like it does every few days–I just destroy the AppVM and make a new one. That’s the same sanitizing effect as closing a disposable. All of my settings are actually on the template because of that funky way Firefox works, so all I have to do is open the new AppVM (which automatically goes to Qtree on its one open tab), log in, and I’m back where I started.
But when my notifier went south, I thought maybe some of my customizations were causing the problem. So, rather than try to undo them, I just created an AppVM based off the bone-stock firefox template. (That takes about 30 seconds. I could have made that into a disposable template, but when debugging it’s sometimes handy not having settings disappear.) I could now visit QTree with an absolutely clean install of Firefox–so clean it opens up the welcome to Firefox tab and the stupid privacy tab–and no worries about my having done something in Firefox to cause the problem. “Try this, Steve.” “No change.” “How about this?” [after blowing away the appvm and creating a new one–like a brand spanking new computer] “No change here either.” It was as if I was reinstalling Firefox, over and over. But I could keep doing it every two or three minutes, all night.
Later on when we figured out all I had to do was log into Wordpus instead of QTree, I could go back to my customized Firefox and try it there, to be sure that that wasn’t the only issue. (AND logic–one of my custom settings could have been hurting me AND I was logging in the wrong way.) I could do this, without having to recreate my settings–by going back to using that VM. I then went back and created a fresh AppVM on that template and made sure it would work that way. So once that worked, I knew the solution would work on a fresh copy of my customized Firefox. At that point, I could consider the problem solved, and I knew the ONLY thing that was wrong before was the login. I didn’t have to change anything else.
Now imagine having to undo all the things Wolf and I tried but didn’t work! Then having to manually reset all of those settings to go back to my “personal” Firefox! No need, when I was working in Qubes, because “delete VM” was doing it for me.
Some caveats and cautions
Although you can create Windows VMs on Qubes, you will have to learn some Linux to use it (if you don’t already know it). At the very basic level, it’s not much to learn. (It has a GUI so you don’t need to learn how to copy files on the command line, or rename them or move them. In fact you can actually use a totally different gui if you don’t like the one it has. The default is called xfce, which is the one that Xubuntu uses so I was very used to it.) If you want to do some more advanced things, though, you’ll have to learn more Linux. I did do some very advanced things, and I know a lot more about Linux than I used to. (Although I wasn’t a complete noob before, I still don’t consider myself any kind of expert even now.)
And if you can’t, no matter how hard you try, keep straight in your head the difference between a TemplateVM and an AppVM, and how you have to make an AppVM into a disposable template to make disposable templates…you’re going to have a tough time of it. (Everyone is going to forget once or twice while learning, of course–that’s not what I’m talking about here. I’m talking about chronically “not getting it.” Or just being the scatterbrained type.)
Another issue is that Qubes OS can be very fussy about the computer it runs on. I wouldn’t do anything you can’t undo installing it…just in case it won’t install and you have to go back to what you had before. (I.e., don’t blow away what’s on the hard drive in your computer installing Qubes…install to a fresh hard drive or SSD, or at least one that’s got crap on it you don’t care about.) Installation for me was a nightmare–QubesOS literally could not interact with my hard drives, including the one I wanted to install it on–but I finally got it to a state where it was running off a thumbdrive and I was able to decide, “Yes I want to do this…so now I have to buy another computer it will work on.”
Whatever machine you decide to use should have a fast CPU on it and at least 32 Gb of RAM in it, and 64 Gb would be much better. And a 256 Gb SSD would be good too (SSDs are faster than regular hard drives), especially if you can get one of those mvne types that plugs directly into your motherboard. I’ve seen people struggle successfully with smaller machines, but if you can possibly afford an appropriate box (or already have one) then you’ll be happier.
(Cthulhu, I have no idea how well it works on Raspberry Pi machines.)
Obligatory PSAs and Reminders
China is Lower than Whale Shit
Remember Hong Kong!!!
https://youtube.com/watch?v=L3tnH4FGbd0
中国是个混蛋 !!!
Zhōngguò shì gè hùndàn !!!
China is asshoe !!!
China is in the White House
Since Wednesday, January 20 at Noon EST, the bought-and-paid for His Fraudulency Joseph Biden has been in the White House. It’s as good as having China in the Oval Office.
Joe Biden is Asshoe
China is in the White House, because Joe Biden is in the White House, and Joe Biden is identically equal to China. China is Asshoe. Therefore, Joe Biden is Asshoe.
But of course the much more important thing to realize:
Joe Biden Didn’t Win
乔*拜登没赢 !!!
Qiáo Bài dēng méi yíng !!!
Joe Biden didn’t win !!!
