File this post under Classes For Patriots: Plausibility 101.
First, the background.
Yesterday, I got into a great discussion with Gail Combs, which began by her pointing out the suicide of a Charlottesville “tiki torch” participant, Andrew Dotson.

I will just warn you that the link provided, which makes a good point about not letting the Alinsky left ISOLATE patriots (loosely defined), is on an arguably neo-Nazi site, the Daily Stormer, and the article is at least in part by a guy who is well-known as a rabid antisemite, and is either a real Nazi or a fake one used to gin up a casus belli for the left. Either way, I feel a bit unclean just letting the site be in my browser.
LINK: https://wqth.wordpress.com/2020/01/16/dear-kag-20200116-open-thread/comment-page-1/#comment-365865
I had a very complex response to this, over two posts, because one cannot talk about anything connected to Charlottesville without dragging in the subject of controlled opposition.
Link 1: Dupes and Suicide. https://wqth.wordpress.com/2020/01/16/dear-kag-20200116-open-thread/comment-page-1/#comment-365929
Link 2: Controlled Opposition and Set-Ups. https://wqth.wordpress.com/2020/01/16/dear-kag-20200116-open-thread/comment-page-1/#comment-365998
The bottom line here is that I was REMINDED by this discussion of some nasty incidents, where I – much like Mr. Dodson – was set up and used. While our circumstances were quite dissimilar in many ways, they were almost identical in the CALLOUS ABUSE of us as individuals in the name of some hidden, self-justified, communist “good” – an “end justifying all means” – a rationalization that allows communists to use people – both allies and enemies – up to and including the point of DEATH.
The biggest difference BEGAN where I refused to take the easy escape route of suicide, but instead bided my time – waiting patiently – LEARNING what I needed – to figure out what in the hell really happened.
Within the larger communist conspiracy in the United States, there thus existed a smaller yet still very large scandal, which I refer to as the Conspiracy to Advance Affirmative Action, or as I typically refer to it in my own shorthand, CA3. It is important to note that I entered this conspiracy as a willing, eager, helpful DUPE. We wanted affirmative action to SUCCEED. We wanted to make sure it did not fail. The problem was, I was also a scientist. I still had certain allegiances to TRUTH PER SE. Not as I wanted it, but as it WAS. So I could not help but note that – when affirmative action showed a HUGE, serious problem – there would need to be a fix. I even had an idea for the fix, based on my own experiences at a different university – where the FIX WORKED (not on Affirmative Action, but on a similar problem of under-prepared students suddenly facing a college environment).
Stupid, stupid me – believing that the EVIL LEFT actually cared about things that were merely their COVER ACTIONS for GAINING CONTROL, POWER AND MONEY.
Well, somebody above me in the conspiracy – the REAL conspiracy – decided that the simplest fix was to get rid of both me and the student who caused the problem. And they had an extremely ingenious way of doing it, too. It all depended on THEM having information which we at the time didn’t realize they had.
It took me quite a while to figure out how all of this worked. But as Q says, FUTURE PROVES PAST.
Much of what led me to understand the larger conspiracy is what happened AFTERWARDS, when people tried to CLEAN UP. I was very fortunate, in that I got a MASSIVE TIP on what was happening, in the form of a failed drugged/hypnotic induction and debriefing which I accidentally remembered, and kept secret. This allowed me to be a step ahead of the MANY people who tried to gather information on CA3 during the next two decades.
LINK: https://wqth.wordpress.com/2019/01/18/deja-woo/
AND THAT, dear friends, is how we are led to the TITLE of this post.
Please Don’t Send Me Bomb-Making Instructions. QAnon is a Peaceful Movement.
Allow me to explain.
In real life, I still have contact or potential contact with MANY of the people who were involved with CA3. That includes people who were involved in ALL phases – the original dupe conspiracy, the larger conspiracy, the “botched take-out”, the “cover-up”, the “information gathering” and the “attempted clean-up” phases. If anybody talks about “events”, they ONLY talk about the “socially acceptable” and publicly known cover aspects of the whole thing. It’s like an iceberg. Ninety percent of what was going on – much of which is covered by NDAs or known/presumed governmental secrecy – not to mention the 50% or greater aspects which are more or less CRIMINAL – dare not be spoken of.
It’s a complicated business. And most of it is UNDERGROUND – where everyone prefers it would STAY BURIED.
Anyway, I was very surprised, recently, to receive an email from one of the more inscrutable players in this drama. You are probably guessing from the title what that email might have contained.
This player is a bit of a geek, and in many ways reminds me of our good friend and fellow patriot cthulhu – somebody with a good education, many interests, vast knowledge, and a quirky sense of humor because of all of the preceding qualities.
The problem with THAT is that it is impossible to tell when this player is serious, joking, or even BEING SPOOFED.
At this point, a further digression is required.
I have received spoofed emails and text messages for YEARS. These are typically ALLEGEDLY from family members and friends. These are not just phishing from people pretending to be banks, credit card companies, and organizations. These are highly sophisticated attempts to manipulate me in one way or another – ways that require a “personal touch”.
I would also add into this, a very interesting pedo entrapment scheme, back during the Clinton years. So I’m familiar with a lot of different Deep State discreditation tricks that involve impersonation.
Sometimes – particularly in “borderline plausible” cases – I will validate (presumably) that this spoofed communication is in fact a spoof. In lawyer-like fashion, I rarely ask that question unless I already know the answer. And I may yet learn something new, even when I DO ask the known question with a known answer.
Sometimes I DON’T ask the question, even when I know the answer.
Are you following me? It’s a complicated business, if you want to stay ahead in the game.

Back to the story.
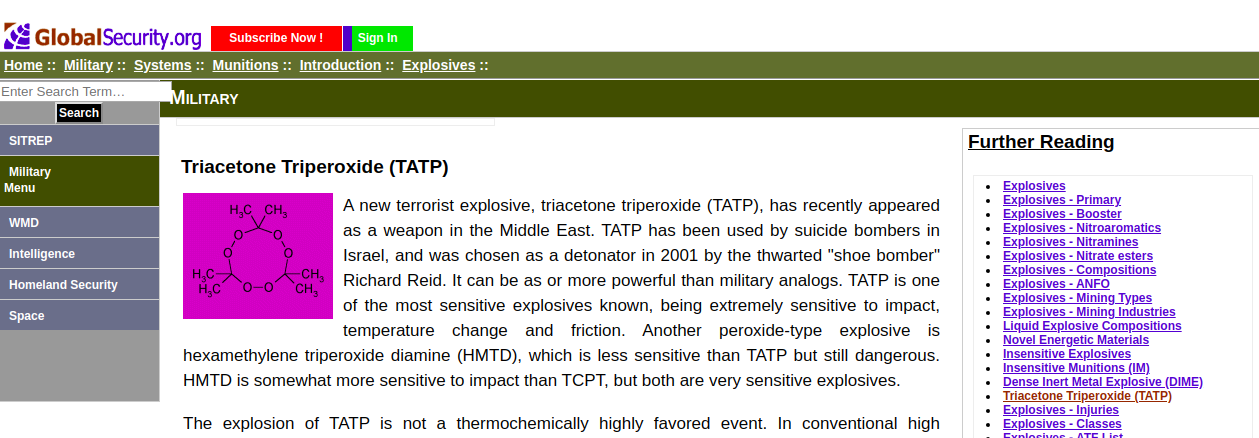
Imagine my surprise when this person sends me an email which appears (from the preview) to be a scholarly article about the synthesis of the jihadist-beloved explosive, TATP, which is either triacetone triperoxide, or tetraacetone tetraperoxide, depending upon one’s sources and nomenclature preferences. And I don’t really want to get into the science of this stuff, for reasons that will appear shortly. But the bottom line, is that I got an email about making TATP.
Yeah. This is well within the plausibility limits of the quirky sense of humor of this person. They send me all sorts of stuff, contradictory and counter-intuitive, contrarian to the max. Sending me a link RAILING about jihadists – and then sending me something like this – is COMPLETELY plausible.
And yet, something BUGGED ME about this email. And I mean REALLY bugged me.
Could it have been a spoof? Maybe. I wouldn’t really know unless I asked. Which meant, I would be asking a question I didn’t at least half-way know the answer to. And I don’t like to do that in dangerous cases. And CA3 is a VERY dangerous case.
I chose not to open the email, and not to call, but instead to wait for some kind of inspiration.
Gail’s comment gave it to me. But I needed to sleep on it.
Last night, I had a dream. It was a complex dream with many moving and changing parts – some familiar, others not. One part of the dream was very interesting. In the dream I traveled somewhere, possibly by plane, or possibly by car or truck. I was in a hotel room. I was sorting through the contents of my large backpack. It was a big pack, suitable for hiking, camping, or other kinds of adventurous outdoor sports (Hi, Gail!). I was concerned about what was in the backpack. As I sorted the contents out onto the bed in the room, one object came out that I had never actually seen in my life. It RESEMBLED an alleged alien folding display device from old, pre-Silicon-Valley UFOlogy. But closer inspection showed it was not that device. It was something else.
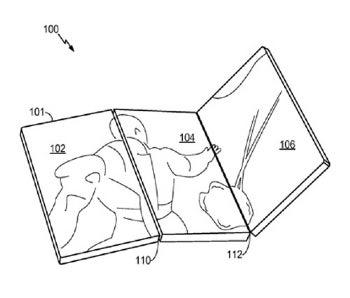
The object was about the size of a thick paperback book. It was something which had been folded up. It consisted of many rectangular panes of a kind of extremely hard plastic, all joined strongly together at the edges with something like a clear, resilient joint similar to tape. It unfolded into a much larger rectangle – a bit like a map.
I tried to understand WTF this thing was. And then it dawned on me.
It was a PORTABLE BLAST SHIELD of some kind. The kind that might be useful for working with explosives outside of a laboratory. Since I had no idea what it was, until I figured it out IN THE DREAM, it had obviously been PLANTED in my pack. And yet, I was now discredited by this thing, which may have even passed through TSA.
At that point, EVERYTHING connected, and I woke up. I understood that I, personally, was now PLAUSIBLY CONNECTED to terrorist explosives.
The other side – and that includes a significant part of the Deep State – is DESPERATE to label the QAnon movement as violent. We are already “discredited” by the Trump campaign itself. Let’s talk about ALINSKY ISOLATION right there.
Whether or not this person intentionally or merely incidentally sent this information about making TATP to me – whether it was well-intended or not – doesn’t really matter.
The fact is, this information is now sitting right there in GOOGLE MAIL. No matter what this person might say to me, there is now a COMPLEX POLYGON OF PLAUSIBILITY which links “manufacture of explosives” to ME, PERSONALLY – and in a way that allows GOOGLE – and we are talking CROWDSTRIKE GOOGLE – to control that information.
Were I to get on a plane – much worse to visit the person in question – and there was an incident of some kind involving TATP – TWO of the primary witnesses most useful to the WHITE HATS in the CA3 matter would be connected to the incident, or worse yet – GONE, GONE, GONE. But that’s not all. The entire Q movement would be immediately discredited as VIOLENT. The enemies of America would suddenly have LEVERAGE they did not have before.
So what is a poor Wolf to do?
Why, this post is what.
So here is the message:

I don’t care who you are – I don’t care what you want. I do not want you to either SEND ME or POST ON THIS SITE any kind of bomb-making information. It is important to protect the reputation of the QAnon movement as NON-VIOLENT.
We love our guns and Bibles, and some of us even love fireworks. Some of us who have actually lived through explosions – like our dogs – may have somewhat less love for fireworks, but we still love our Star Spangled Banner – maybe even more than most, because we understand the PRICE PAID in seared and torn-up flesh to hold up that beautiful Flag.
But we are NOT TERRORISTS, and we are NOT BOMBERS, and we are NOT VIOLENT. We do not want our beautiful movement to be TAINTED with this sort of stuff. So TAKE CARE what you SEND or POST, because WE CARE.
Are we good?
HELL YES, WE’RE GOOD. BECAUSE WE’RE THE GOOD GUYS. AND GIRLS.
W

/THE_END