Thanks to Darren Beattie, Elon Musk, and Gail Combs, I have been struck by lightning, and can now see the origins of the highly successful “trust and safety” censorship paradigm.
I survey the catastrophe that “Trust & Safety” has been for not only Twitter and Apple, but all of Big Tech, America, and the world, and I cry out “Well played, CCP! Well played!”
And you, my fellow coders who watched it all turn to crap, know I’m right. We did not object to the early assaults on Free Speech, as CHINA slyly moved into our tech businesses, and now we have paid the price.

Or if we really want to be complete…..
The part about “can’t code” welcoming in the Trojan Horse is important. In my opinion and experience, it was the non-coding “verbal world” of bureaucratic policy which welcomed “trust and safety”, then forcing it on the more mathematical geek world which had once been a bastion of honesty, truth, and freedom.
Free speech mattered to old tech. Not so much to the people who took control of tech.
This is relevant, in that WOMEN tend to show up as the cops, police chiefs and ambassadors of “trust and safety”. It’s a very female and “beta male” thing, even at the high levels.
BEFORE ELON:

After Elon:

Yeah, those pictures are a bit of an unfair comparison, because they’re different company functions as well, but in other ways, that in itself is exactly the problem.
Coders versus the people who tell them what to do. Twitter was filled with chiefs and not enough Indians.
ALTHOUGH perhaps one too many……
Yoel Roth’s problems don’t end with his refusal to “manspread” like a man, but the problems surely start there. Any “man” who is threatened by the Babylon Bee needs help, not power.
BUT BACK TO THE ACTUAL STORY…..
Trustina Applegate
Darren Beattie of Revolver News had one of the biggest stories yet on censorship in Big Tech.

Turns out that Eric Holder’s former chief of staff was the head of censorship at Apple for quite a while, including the 2020 election.
Here is the brief version of what happened. Please go to the original for the full story. I am only including a highly edited snippet of the middle of the story (and yet it’s VERY long).
FTA…..
The current head of Apple Trust and Safety is someone who is clearly aware of the value of having a low profile online. Look for details on Jessica Gimarc-Savini and you’ll find her sparse LinkedIn page, her (lesbian) wedding page, and not much else.
While we know little about Jessica Savini, we can learn much from a profile of her predecessor, former head of Trust and Safety at Apple Margaret Richardson.

Richardson served as Apple’s top trust and safety figure from August 2020 through May 2022.
As you read the following, keep in mind that Apple is the largest company in the world, with a market capitalization of $2.3 trillion dollars. Its annual revenues exceed the GDP of most U.S. states. It’s annual net profits are worth more than the GDP of Bulgaria. Apple might as well be a country unto itself, and a powerful one at that. Of all of the people they could have chosen to be the key decision maker for content moderation and safety — that is, censorship — you’d think they’d at least choose someone with the appearance of moderation and lack of political bias.
Think again.
While Richardson wisely avoided tweeting during her tenure at Apple, at her previous job, first as “director of global policy” and then “director of trust” as Airbnb, Richardson was entirely unrestrained. Her still-extant tweets from August 2020 and before give a stark demonstration of her thinking, a perpetually-spinning hamster wheel of stock left-wing political tropes. For starters, Richardson’s Twitter banner screams “Black Lives Matter”!

But that’s only scratching the surface.
Dig back through 5+ years of tweets and retweets, and you see a type that is disturbingly common: A person’s whose public life consists almost wholly of mindlessly affirming, then reaffirming, and then re-reaffirming, far-left and liberal partisan orthodoxies.

It’s not that any one tweet from Richardson is particularly bad. It’s that that’s all there is. She never strays into talking about her family or her favorite books or even, say, her favorite vacation spots (she was working at a lodging company, after all!). It’s just the current partisan lib obsession du jour, every time, with ruthless tedium.
Richardson isn’t just deeply ideological, pro-BLM, and so forth. She’s also narrowly and almost pettily partisan.
If this was your barista at Starbucks, or a Congressional staffer, or heck, an ordinary Apple engineer, this would be rather lame but unremarkable. But this is the person Apple chose to lead its Trust and Safety division, the person chosen to be head censor at the most powerful company in the world. This is the person who was empowered to make crucial, politically-loaded decisions during one of the most hotly-contested elections in American history.
Five months after Richardson started at Apple, the company made one of the most ideologically aggressive cancellations ever when it banned Parler from its app store. While Apple works hard to obscure its decision-making process, Richardson was without a doubt central to that decision, and with her involved, it wasn’t a surprising one. In April 2022, shortly before she left, the company also committed itself to a ridiculous internal “racial equity audit.”
So, where did this person come from? Well, just looking at her tweets, one notices that Richardson doesn’t just have a habit of boosting left-wing causes. She has a noticeable preference for boosting senior figures from the Obama Administration itself — Valerie Jarrett, Arne Duncan, John Kerry, and so forth. Richardson was particularly active when President Trump dismissed acting attorney general Sally Yates for insubordination after she refused to enforce his executive order implementing a travel ban on several nations linked to Islamic terrorism.

This isn’t random.
After earning dual degrees in law from UC-Berkeley and in public policy from Harvard’s Kennedy School, Richardson spent three years working at a free legal clinic in the Bay Area. From there, she went to the Obama campaign, and after his election she joined the Justice Department as a top adviser to Eric Holder, eventually ascending to become his chief of staff.
Wolf again….
SO – I hope that is crystal clear.
The Obama-Holder DOJ directly controlled Apple’s view of “acceptable content” during the engineered fall of the Trump administration (a.k.a. “The Coup”) as well as first two years of the Biden administration.
This is exactly why I absolutely cannot stand Apple News, for it’s horrible, judgmental, left-wing slant.
If you read the rest of the Revolver article, it is VERY clear that the “Trust and Safety” racket is largely an infiltration of Big Tech by an ideology centered on Eric Holder and the DOJ.
In my opinion, Trust & Safety in Big Tech was ultimately a downstream effect of the disastrous Obamacare website, which was used to “lure in” Big Tech for what became an infection operation.

People who had no idea how to deal with criminals and communists were sheep led to the slaughter.
SO – back to Twittergate.
I didn’t really make the connection of Twitter’s “Trust and Safety” machine to DOJ, until Elon Musk revealed The Twitter Files to the world, via left-trusted journalist Matt Taibbi, in a massive act of transparency.
Somewhere in the middle of Matt Taibbi’s tweet-thread, I realized that Apple and Twitter were undoubtedly similar stories – and that Eric Holder likely had an insider at Twitter.
Allow me to interject with a meme here…..

Moving on…..
But THIS is where the DOJ comes back into things. The next tweet (28) is like discovering Eric Holder working at Twitter.
Jim Baker? You mean SPYGATE Jim Baker???
I had figured there was some Holder groupie analogous to Richardson at Apple, inside Twitter’s Trust & Safety apparatus. I had no idea that Holder’s henchman – THE Jim Baker, fired as part of Spygate – was there.
Let’s just look at that Jim Baker message more closely…..

This is an incredible stall tactic. Twitter can hold off the truth forever with this thinking.
Note how the “hacked materials” policy is already anti-journalism, but combine it with a DOJ Obama/Hillary toadie INSTALLED INSIDE TWITTER, and, it’s every bit like Apple. Complete DOJ commie control.
SO – it’s clear that “Trust and Safety” is a DOJ gig – right?
How could this possibly be worse?
The trick is understanding the “environmental push” for “Trust and Safety” over free speech, which overwhelmed both government and tech. It almost certainly had foreign help.
Gail Combs Exposes Trust-and-Safetygate
Today, Gail posted a series of deep dives into the subject of where much of the “trust and safety” censorship has appeared and festered in both government and Big Tech – spilling over into everything, including elections, journalism, STEM, and even White House policymaking.
The big picture blew me away, as I saw how successful this movement was, in transforming our own government and national security complex away from freedom and toward CCP-style totalitarianism, without even being fully understood by the victims.
Some of the CCP infiltration is obvious – some of it is not.
I present it to you now, largely unedited except by Gail herself, in preparing it for this post. I have also taken the liberty of embedding the videos by hand, rather than just leaving links. I have further included some comments that Gail left out, because I feel they are still important, even though she did not.
LINKS TO SELECTED ORIGINAL COMMENTS:
Online
Coyote
Reply to WSB
December 5, 2022 07:14
From BadKitty’s Thread — The KEY INFO showing GOVERNMENT CENSORSHIP IMPACTING ELECTIONS!!!
They also submit reported tweets to CISA at DHS. Boom!
DHS puts on its CISA website for election misinformation, disinformation, and malinformation to be reported to Misinformation@Cisecurity. (NGO Katie Hobbs used for reporting.)
RUMOR CONTROL PAGE START-UP GUIDE Misinformation, disinformation, and malinformation (MDM) can present risks to the election infrastructure community, its owners and operators, and the public. MDM can spread quickly, causing rumors to undermine facts.
The risks of MDM range from undermining confidence in institutions to activating and inspiring dangerous behaviors and violence. This Rumor Control Page Start-Up Guide is for organizations seeking to dispel specific MDM narratives through transparent and authoritative information. Designed for use by state, local, tribal, and territorial (SLTT) government officials and private sector partners, this guide cites the Cybersecurity and Infrastructure Security Agency’s (CISA) Rumor Control page as a model for debunking inaccurate narratives. The recommendations in this guide are not intended to be one-size-fits-all and should be adapted to the capabilities and resources available, as well as the MDM risks facing the community. Organizations should only set up a rumor control webpage related to issues for which they have access to information and expertise necessary to properly dispel MDM narratives and articulate facts. Each organization that plans to set up a rumor control page may want to consult with the appropriate organization legal counsel, if possible, prior to beginning operations. What is a rumor control page? A rumor control page is a web page that offers the public accurate and authoritative sources of information which will help address common MDM narratives. It is provided by a trusted voice to either preempt or respond to developing narratives. Credible messengers are most effective at disproving falsehoods. A rumor control page should not be considered the sole source of truth, rather it should drive people to seek more information about a complex subject by directing them to other trustworthy sources.
With a rumor control page, election officials and stakeholders can dispel rumors about the systems and assets they manage and have unique insight into. Some election offices may already have public information websites, which commonly include a “Frequently Asked Questions” page and/or press releases that seek to clarify information. In this sense, a rumor control page can be viewed as an extension of existing efforts….
It is important to note that a rumor control page is only one element of a successful MDM response strategy. Improving resilience of elections to MDM also requires reporting MDM narratives. The Center for Internet Security (CIS) was established to support the cybersecurity needs of the election subsector. The CIS can be leveraged to report real-time MDM via email at misinformation@cisecurity.org
Be sure to include links and screenshots as well as details on the misinformation and your jurisdiction.
7
Reply
Online
Coyote
Reply to Gail Combs
December 5, 2022 07:44
Don’t miss Bad Kitty’s other thread.
CCP involved with Carnegie…
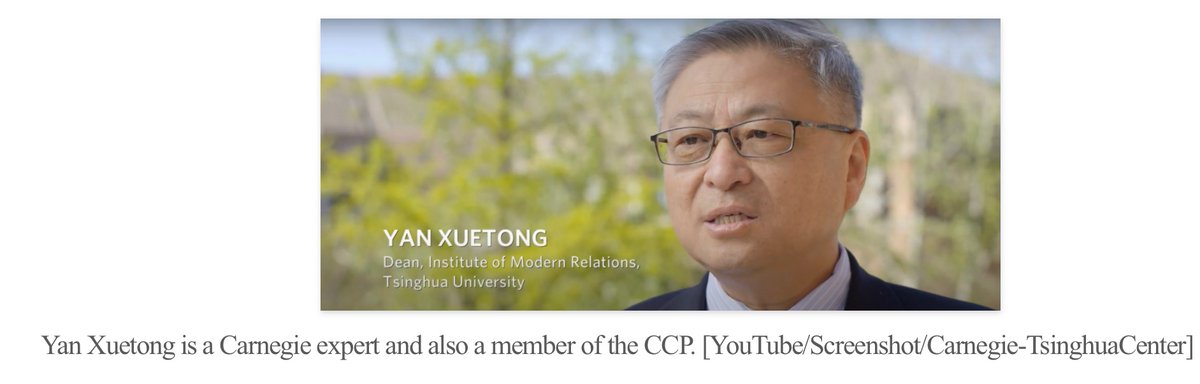
Multiple former Chinese gov employees and at least 20 CCP members worked at Carnegie Endowment while CIA DIR William Burns was pres 2015-21
They are closely associated with CUSEF (reg under the Foreign Agents Registration Act as a Chinese foreign gov org)
Last edited 12 hours ago by Gail Combs
7
Reply
Online
Coyote
Reply to Gail Combs
December 5, 2022 07:52
- Texas Republican Rep. Lance Gooden called on CIA Director William Burns to address his “strong ties” to the Chinese Communist Party (CCP) while formerly heading an elite Washington, D.C., think tank, according to a letter obtained by the Daily Caller News Foundation.
- At least 20 undisclosed CCP members worked at Carnegie Endowment for International Peace during Burns’ presidency of the think tank, the DCNF recently reported.
- “Evidence would suggest Director Burns lied under oath during his confirmation hearing,” Gooden told the DCNF, referring to Burns’ February 2021 CIA confirmation hearing.
Texas Republican Rep. Lance Gooden called on CIA Director William Burns to address his “strong ties” to the Chinese Communist Party while formerly heading an elite Washington, D.C., think tank, according to a letter shared with the Daily Caller News Foundation Monday….
“The vast influence the CCP had at Carnegie during your tenure as president and the continued influence they have today — despite claims you made at your confirmation hearing that you had ended the CCP’s influence — presents a significant lapse in judgment and brings into question your ability to identify and mitigate national security risks,” Gooden’s letter said. (RELATED: Biden’s New Green Energy Adviser Has Ties To Chinese Communist Party Front Group)
There is a lot of information coming out and We want to capture it before it disappears.
First a Youtube from August 25, 2020 just before early voting started.
Are We Ready? Foreign Interference, Disinformation and the 2020 election
Streamed live on Aug 25, 2020
Public and private sector leaders join the Digital Forensic Research Lab of the Atlantic Council to discuss what steps they have taken to secure the information space around the 2020 presidential election. For further information, please visit: https://www.atlanticcouncil.org/event…——————————————————————————————– Subscribe for more! https://www.youtube.com/user/Atlantic…
Driven by our mission of “shaping the global future together,” the Atlantic Council is a nonpartisan organization that galvanizes US leadership and engagement in the world, in partnership with allies and partners, to shape solutions to global challenges.
LINK: https://www.youtube.com/watch?v=rUDHdwSwQFQ
After looking at part of this video I decided to investigate the people named. This is my research.
March 26, 2018
DHS hires new cybsersecurity adviser ahead of 2018 midterm elections – Washington Examiner
The Department of Homeland Security has hired the former chairman of the Election Assistance Commission, Matt Masterson, to help federal, state, and local authorities coordinate cybersecurity efforts ahead of the 2018 midterm elections, the department announced Monday.
Masterson will serve as senior cybersecurity adviser within the National Protection and Programs Directorate’s Office of Cybersecurity and Communications.
“There are few who have Matt’s experience working with all levels of government and the private sector to protect our nation’s election systems. His wealth of experience and depth of knowledge make him highly respected on both sides of the aisle,” Chris Krebs, NPPD senior official performing the duties of the undersecretary, said in a statement.
Krebs added that Masterson’s previous work as chief information officer in the Ohio secretary of state’s office and at the EAC “significantly advanced” the country’s cybersecurity efforts.
Matthew Masterson Joins DHS as Senior Cybersecurity Adviser
Matthew Masterson, former chairman of the U.S. Election Assistance Commission, has been named senior adviser for the Department of Homeland Security‘s cybersecurity unit, Washington Examiner reported Monday.
DHS expects Masterson to continue working with federal, state and local officials to protect election systems against cyber threats.
He served as EAC commissioner for nearly four years, following his nomination by then President Barack Obama and subsequent confirmation by the Senate in late 2014.
Masterson previously held various positions within the Ohio secretary of state’s office, where he managed voting system certification procedures and led the development of online voter registry and ballot delivery platforms for military and overseas voters.
Christopher Cox Krebs (born 1977) is an American attorney who served as Director of the Cybersecurity and Infrastructure Security Agency in the United States Department of Homeland Security from November 2018 until November 17, 2020 when President Donald Trump fired Krebs for contradicting Trump’s claims of election fraud in the 2020 presidential election.[1]
Clara Tsao
Clara Tsao is a nonresident fellow with the Atlantic Council’s Digital Forensic Research Lab. Clara is a national security and disinformation expert and technology entrepreneur currently serving as the co-founder and on the board of the Trust & Safety Professional Association and the Trust & Safety Foundation. Clara previously was the Senior Advisor for Emerging Technology at the Department of Homeland Security and the Chief Technology Officer of two U.S. Government task forces focused on countering foreign influence, election security, and homegrown extremism. Clara also serves as a nonresident expert at the German Marshall Fund, a senior advisor for the UN-backed initiative, Tech Against Terrorism, and the President/Chair of the White House Presidential Innovation Fellows Foundation. Clara has also held fellowships focused on national security and technology policy with the Mozilla Foundation and Google.
June 26, 2020
The Brief: Clara Tsao’s newly-launched Trust & Safety Professionals Association
Clara Tsao is Cofounder of the Trust & Safety Professionals Association (“TSPA”), a new, nonprofit, member-based organization for trust & safety professionals that launched in June 2020. The TSPA will support the global community of professionals who develop and enforce principles & policies that define acceptable behavior online.
Clara was inspired to build an association for trust & safety professionals due to her background as a national security/disinformation expert and technology entrepreneur. She is President of the White House Presidential Innovation Fellows Foundation and a Senior Advisor at the UN-CTED-backed Tech Against Terrorism.
Clara has held various national security and tech policy roles for the U.S. Government, Google, and Mozilla.
most of the page is just icons with very few words. I wondered if she was a non-native English speaker while Hubby suggested it was a method to prevent word searches.
Her Awards/honors/networks section shows:
Fulbright Canada
Clinton Global Initiative
Hesslbein Global Academy
Pembroke College Cambidge
Univ California
United Nations: Many Cultures One Humanity – Linked to spam
Alliance of Civilizations – Linked to spam
GES Malaysia 2013 – Linked to spam
Global Startup Youth Malaysia – Linked to spam
Yale School of Management [Emerging Leaders Seminar Entrepreneurship & Innovation] – Access denied
TITLE – Global Network for Advanced Management
Clara Tsao | Presidential Innovation Fellows
Clara Tsao is an entrepreneur and a White House Presidential Innovation Fellow. Prior to government, she led global strategic partnerships in education for Microsoft. In addition to corporate roles with Google, Apple, Sony, Playstation, HP, and AT&T, Clara is also the co-founder and former Executive Director of the Congressional App Challenge.
Clara Tsao – Guidance on building better digital services in government
Through the Presidential Innovation Fellows program, Clara has worked across various national security roles in US Government, serving as a senior advisor and Chief Technology Officer focused on emerging technology policy, countering terrorist use of the internet, and foreign influence operations online. News and Events
ALLIANCE For SECURING DEMOCRACY:
About Clara Tsao
Clara Tsao was a non-resident fellow at the Alliance for Securing Democracy. She is an online disinformation expert and a civic tech entrepreneur, who recently co-founded the Trust & Safety Professional Association and the Trust & Safety Foundation to support the global community of professionals who develop and enforce principles and policies that define acceptable behavior and content online. Clara is also a non-resident senior fellow at the Atlantic Council’s Digital Forensic Research Lab. Her previous roles include CTO at the U.S. Department of Homeland Security’s Countering Foreign Influence Task Force and the interagency U.S. Countering Violent Extremism Task Force and Senior Advisor for Emerging Technology at the Cybersecurity Infrastructure Security Agency. She has spent a decade working in the technology industry across global teams at Microsoft, Apple, Sony PlayStation, AT&T, and also as a Google and Mozilla Technology Policy Fellow. Clara is also the Board Chair and President of the White House Presidential Innovation Fellows Foundation and a Senior Advisor at Tech Against Terrorism.
This may be her (Her resume has been erased)
https://www.claratsao-design.com/about
(UI/UX Designer From Taiwan)
There is NOTHING about her early history and where she was born. CHINESE maybe?? Does she actually work for the CCP?
MUST READ about her views on ‘Disinformation’ Interesting tidbit”…we need to encourage more technologists to lend their expertise to support better policy-making, through incubators like Aspen’s Tech Policy Hub….”
…..Much of your current work lies at the intersection of tech and policy, focusing on issues like disinformation and online safety. How did you first become interested in these issues?
JFK once said, “We choose to go to the moon in this decade and do the other things, not because they are easy, but because they are hard, because that goal will serve to organize and measure the best of our energies and skills, because that challenge is one that we are willing to accept, one we are unwilling to postpone, and one which we intend to win.” In a similar way to how JFK committed the nation to the ambitious goal of landing on the moon,I believe the field of “trust and safety” (including online safety / disinformation), is the most difficult challenge of this decade that technology companies, governments, civil society, and internet users must stand united behind.
This is a challenge we need to win. From live-streamed mass shootings, terrorist content, online sexual exploitation and conspiracy theories, to election interference, there are endless problems that require collaboration, starting with strengthened dialogue. I have always been fascinated with how people behave online, and I spend my free time evaluating how people behave on social media. I especially love testing and exploring new technology platforms to understand the new ways in which people interact and connect with one another.
However, I was first exposed to the offline consequences of fake news and misinformation while I was at Microsoft in early 2014. At Microsoft I was managing a partnership program focused on growing the capacity of libraries in Myanmar to serve as trustworthy information hubs. We piloted new platforms and approaches to tackle digital and information challenges in the lead-up to the country’s critical 2015 general elections, the first time the nation could participate in a democratic vote after nearly 50 years of military rule. Over the span of months,I saw firsthand the impact of rampant disinformation as Facebook unintentionally introduced the country to a new digital era that causing offline chaos, violence, and eventually, ethnic genocide.
Years later, I joined the US Government as an Entrepreneur-in-Residence’ where I served as the CTO of two teams within the Department of Homeland Security focused on online safety issues, ranging from terrorist use of the internet, to foreign influence operations and election security. Most recently, I worked with human rights defenders, civil society groups, and policy professionals at Mozilla, evaluating regulatory policies and tools around harmful content online. My Passion for problem solving in this space was cultivated by these experiences.
What particular questions/challenges have you been tackling recently, and why is now the right time to address these?
Over the last year, I have been building a new organization to support and advance the trust and safety profession through a shared community of practice. Today the biggest challenge in trust and safety is the lack of formalized training and support for the professionals that determine and enforce acceptable content policies and behavior online.Professionals working in trust and safety teams at technology companies are tasked with adjudicating what is acceptable behavior or content, while also protecting free speech, user safety, and society. Trust and safety teams are also asked to make difficult decisions to protect users, while also having limited support from product and engineering teams to carry out and enforce these policies at scale.
There has never been a better time to support trust and safety professionals and to do their best work. Due to recent media coverage of content moderation, there has been more awareness of the psychological and mental health risks associated with content review that impact employee wellness.
As fake news and misinformation has gone rampant in election processes, governments around the world have threatened regulation or fines for the inability of timely content review and removal. Some countries, like Germany, have introduced and are enforcing such regulations. Hate speech that stays online in Germany for more than 24 hours can accrue a fine of €50 million under Netzwerkdurchsetzungsgesetz. Examples like these have led companies to invest more resources in their trust and safety operations and have more transparency in their decision-making practices.
Furthermore, technology companies are increasingly realizing the impact that toxic users and behavior have on “user churn” and bottom line.
“Advertisers like Unilever have threatened to take their marketing budgets elsewhere if platforms don’t mitigate the spread of toxic content or toxic users.”
Are certain types of misinformation more dangerous than others? What criteria should companies use to evaluate whether a piece of content should be removed from their platform as misinformation?
The perceived danger of misleading content is a key element that influences the way many companies prioritize and investigate removal. Misinformation can include false or misleading information, ranging from rumors, gossip, errors, propaganda. While misinformation can be harmless (i.e married celebrity having an affair), information can become dangerous when the content has offline or behavioral consequences for users and goes viral (i.e. drinking diluted bleach will prevent you from COVID-19 infections).
When evaluating misinformation, companies can evaluate the actor behind the campaign, the behavior of the post (is it a bot network?), and the context of the content to determine how to prioritize removal. Other times, misinformation is automatically detected by AI/machine learning or flagged manually by users reporting the post
One challenging part of misinformation is when content is further bolstered by recommendation engines and algorithms, originally designed to heighten user engagement but now leaving users in partisan and polarized filter bubbles.
When Someone searches for content reinforcing fake science such as the flat earth theory, they become stuck in a “rabbit hole”of other conspiracy theories unknowingly, of which many include content from the anti vaccine movement. To Counteract this, AI researchers like Guillaume Chaslot have advocated internet platforms to have increased algorithmic transparency.…
>
ALICIA WANLESS

Australian Strategic Policy Institutes
Alicia Wanless is the director of the Partnership for Countering Influence Operations at the Carnegie Endowment for International Peace.
Alicia researches how people shape — and are shaped — by a changing information space. With over a decade of experience in researching and analyzing the information environment, focusing on propaganda and information warfare, Wanless applies this learning to support government, military, and major tech companies to develop policies and integrate information activities into training programs that better reflect how the information environment is manipulated.
Wanless is currently a PhD Researcher at King’s College London exploring alternative frameworks for understanding the information environment.
In 1836, King’s became one of the two founding colleges of the University of London…
Biography
Alicia researches how we shape — and are shaped — by a changing information space. With more than a decade of experience in researching and analysing the information environment, focusing on propaganda and information warfare, Alicia conducts content and network analysis, and has developed original models for identifying and analysing digital propaganda campaigns. Alicia applies this learning to support government, military and major tech companies to develop policies and integrate information activities into training programs that better reflect how the information environment is manipulated. She has shared her work and insights with senior government, military, industry leaders and academic experts at Wilton Park, the Munich Security Conference, the Hedayah Centre, NATO’s ARRC and the Lawrence Livermore National Laboratory. Alicia’s work has been featured in the CBC, Forbes, and The Strategy Bridge
LAWFARE: Alicia Wanless – Contributors – Lawfare
Jan 20, 2022
Alicia Wanless is the director of the Partnership for Countering Influence Operations at the Carnegie Endowment for International Peace. Wanless is a PhD Researcher at King’s College London exploring how the information environment can be studied in similar ways to the physical environment.
Her twitter account is PRIVATE….
https://twitter.com/lageneralista
This interest led me to research things like nationalism, propaganda, and language engineering in my undergrad, and later in the 2010s, to start analyzing how influence operations were changing in a Digital Age. That research, which covered political campaigns and alternative media outlets, led me to work with militaries, major tech platforms, and civil society organizations—and ultimately to pursue a Ph.D. in War Studies at King’s College London….
The disinformation landscape surrounding the 2020 elections was so different than what we saw in 2016, with domestic, verified users supplanting bots and fake accounts, and new narratives focusing on both Covid and electoral fraud. The actors, behaviors, and content keep changing. How do you see the disinformation landscape evolving in the future?
I’m not sure it’s the information environment changing quickly so much as our focus on what happens within it shifting. In researching the U.S. primary election in 2016, it was apparent that domestic actors were likely far more active and prevalent than any foreign actors, and this was later confirmed in Benkler, Faris, and Roberts’ Network Propaganda. The disclosure that Russian actors were actively running influence operations made for more shocking news, whereas disentangling the complex web of domestic actors can be difficult and highly politicized. The role of domestic actors engaging in influence operations has certainly come to the fore in the wake of the attack on Congress on 6 January.
One major challenge in understanding the information environment is that research tends to focus on threat actors, tactics, and the content they produce, often in the form of case studies— interesting and informative, but fairly narrow in scope. Unless it is all brought together in bigger meta studies, it leaves us focused on the last bad thing that happened, which is not great for being strategic about addressing the problem. To that end, I think we need to move towards a more systemic understanding about disinformation and influence operations, looking at the wider information environment in which these things occur to find patterns that might offer a warning where the next problem is emerging. That would allow us to intervene sooner.
Some of the information from the BadKitty Thread:
LINK: https://threadreaderapp.com/thread/1599609708574543873.html
Breaking thread! I found the directions for submitting tweets to El-ISAC (CiSecurity) like Katie Hobbs did. They land at Stanford for determination
There is also a hidden Twitter Portal and a gov Twitter email address.😹
https://pbs.twimg.com/media/FjLxKJWWIAAnyc0.jpg (see below)
The Stanford Partnership site that fact checks submitted tweets etc:
1. It’s home page changed dramatically in months.
2. They lied and said Trump supporters went to J6 Armed.
3. They work with the Zinc Network/Integrity Initiatives Graphika and DFRLAB.

LINK: https://archive.ph/GdkGR

I missed putting the biggest part in the top tweet because I was eating ham salad crackers. And ran outta edit time.
They also submit reported tweets to CISA at DHS. Boom! 💥
DHS puts on its CISA website for election misinformation, disinformation, and malinformation to be reported to Misinformation@Cisecurity. (NGO Katie Hobbs used for reporting.)
https://www.cisa.gov/sites/default/files/publications/rumor-control-startup-guide_508.pdf


It is important to note that a rumor control page is only one element of a successful MDM response strategy. Improving resilience of elections to MDM also requires reporting MDM narratives. The Center for Internet Security (CIS) was established to support the cybersecurity needs of the election subsector. The CIS can be leveraged to report real-time MDM via email at misinformation@cisecurity.org
Be sure to include links and screenshots as well as details on the misinformation and your jurisdiction.RUMOR CONTROL PAGE START-UP GUIDE Misinformation, disinformation, and malinformation (MDM) can present risks to the election infrastructure community, its owners and operators, and the public. MDM can spread quickly, causing rumors to undermine facts. >> The risks of MDM range from undermining confidence in institutions to activating and inspiring dangerous behaviors and violence. This Rumor Control Page Start-Up Guide is for organizations seeking to dispel specific MDM narratives through transparent and authoritative information. Designed for use by state, local, tribal, and territorial (SLTT) government officials and private sector partners, this guide cites the Cybersecurity and Infrastructure Security Agency’s (CISA) Rumor Control page as a model for debunking inaccurate narratives. The recommendations in this guide are not intended to be one-size-fits-all and should be adapted to the capabilities and resources available, as well as the MDM risks facing the community. Organizations should only set up a rumor control webpage related to issues for which they have access to information and expertise necessary to properly dispel MDM narratives and articulate facts. Each organization that plans to set up a rumor control page may want to consult with the appropriate organization legal counsel, if possible, prior to beginning operations. What is a rumor control page? A rumor control page is a web page that offers the public accurate and authoritative sources of information which will help address common MDM narratives. It is provided by a trusted voice to either preempt or respond to developing narratives. Credible messengers are most effective at disproving falsehoods. A rumor control page should not be considered the sole source of truth, rather it should drive people to seek more information about a complex subject by directing them to other trustworthy sources. >>With a rumor control page, election officials and stakeholders can dispel rumors about the systems and assets they manage and have unique insight into. Some election offices may already have public information websites, which commonly include a “Frequently Asked Questions” page and/or press releases that seek to clarify information. In this sense, a rumor control page can be viewed as an extension of existing efforts….
ADDED NOTE BY WOLF
This stuff is just off-the-charts suspicious to me.

The Big Picture – CCP Subversion and Influence

I’m going to let people draw their own conclusions here. I’m not going to do anything other that talk about my own experiences with Chinese spies and assets in tech. You do the math.
It is beyond any doubt that the CULTURE of “trust and safety” is off-the-charts CCP in tone. There is SMOKE everywhere. And where there is smoke, there is probably fire.
It is my suspicion that “trust and safety” is filled with CCP-bots of various kinds, both Chinese and non-Chinese. However, diagnosing a spy from a non-spy is difficult, and requires an enormous amount of personal knowledge. I may have suspicions, but they are little more than that. Some may think I have TOO MANY suspicions, and that is fine.
However, it is my opinion that anybody with a potential CCP spy or asset background (thus including non-Chinese Americans) who strongly advocates or (even more tellingly) creates outcomes for things which serve CCP’s interests, and which oppose freedom-loving Americans’ interests, needs to be treated as such, particularly in regards to sensitive information or access. Just my opinion.
CCP loves to use women spies, operatives, and agents of influence, just like CIA. CCP girl spies are not just out of the mainland – many come out of Hong Kong, Taiwan, Singapore, Malaysia, Indonesia, Japan, England, Canada, America, and Latin America. Having them come out of somewhere other than the mainland, gives them a lot of flexibility, by lowering people’s guard and defenses.
CCP girl spies are smart, and the ones in tech tend to be excellent at both the coding side AND the schmoozing, verbal, business and policy side. They will sometimes HIDE one side of their abilities, if that deception is useful. However, in many cases, they will leverage both sides openly.
ChiSpies are often (but not always) among the most relentless social climbers you will ever meet. It’s the job – get as high as they can, targeting higher and higher up the chain. The Russian spies Maria Butina and Anna Chapman were the same way. I saw this much more often with the women than the men. The men tended to be far less obvious in trying to make new connections, whereas the women were extremely socially focused.
Many CCP spies are what I call “two-steppers”, which involve two generations of family as a form of cover. The parents may appear in America as refugees or economic migrants, being apolitical or (less often) even anticommunist. They may come from a place or background which throws off suspicion. The child, however, ends up in a sensitive position, and engages in actions, both of which clearly serve CCP interests. Thus, “two steps” to achieve a solid and easily dismissed infiltration.
CCP spy girls will often change their stories quickly and believably when questioned. They are quite good at planting false or compromising background information in social networks, although men tend to be used when planting something directly to another man, as a technique of peer influence.
Washington is the perfect environment for CCP players, because the operatives don’t stick out. The culture is one of influence and networking, so it looks like everybody else. ChiSpies tend to stick out more in the hinterlands.
Non-Chinese who carry water for CCP can be of many different types. Many are CCP allies, such as old Russian communists, American leftists, American rightists with economic ties to China, or dupes who become personally or professionally involved with agents.

It is important to understand that CCP operatives can have dramatically negative effects on other nations without doing ANYTHING illegal. I saw this form of stealthy sabotage over and over in tech. Just by burying into a key position and turning into an unremovable goldbrick, a CCP operative can create negative effects that have an organization chasing its tail. With only a bit more effort, such as engineered incompetence, organizations can be made weak, unprofitable, and ripe for takeover.
I put the “Trust and Safety” movement in this category of organizational sabotage. I think this entire movement serves CCP goals, and not American interests.
Others may disagree. They may assert that China helped America, if anything, by supporting “trust and safety” in any ways that it did, such as by providing “moderation” services.
To those who might think so, I simply add one more “unit” to my previous assessment of “4”.
W










An amazingly detailed argument, with which I agree. Trust and Safety probably was devised as a way to usher in Chinese influence. On the most basic level, the name is calculated to make us think we can trust the government to keep us safe.
It is bound to be filled with bots. I think the level of Chinese infiltration is off the charts. It “helps” when we have high-level politicians in league with them.
Yup. You’re right. Now I can see it. That’s the reason the infiltration is so thick. Non-Chinese INSIDERS positioned so frequently and so high in the overall scheme. They (CCP) can just swarm in. Biden is exemplary.
It wasn’t made public either, it was buried with an opaque bureaucracy. No one knows what “trust and safety” is (yes a blatant CCP scheme!!!) Just that “Twitter” or “Facebook” did this or that…
They admire the Chinese model of social control. Diversity for thee, not for me. They like and need diverse STAFF, but only as subordinates:
https://www.atlanticcouncil.org/about/board-of-directors/
Good GRIEF. That page reads like the Halls of 9/11. Every goon that went after Trump. Now it all makes sense. This is why “Never Trump”. Enough of that board would be kicking air for the truth coming out, that the whole org will “do anything” to stop Trump.
Just in case anyone forgot…
BUSTED: Mike Pompeo Says He Has List of American Governors Named as ‘Friendly’ by Communist China
The Q strategy was brilliant in this regard.
They knew the DNCCP had burrowed themselves deep within the Twitter superstructure.
They knew Team Trump could object to Twitter policing and got exactly nowhere.
How could they hold Twitter accountable?
They would need an army of active accounts
An army of Digital Soldiers operating as a combantant command
They would need an external, independent, reliable C&C rally point.
Just like the DNCCP submitting objections to Trust and Safety to get things “handled”… Team Trump would have a powerful virtually unstoppable method of holding the extreme Twitter manipulation and power players accountable
It would work up until the point where the digital warfare escalated that Twatter was FORCED to mass evict accounts on their platform
No matter the reputational or psychological costs involved
It forced them to play they’re hand, the CCP Playbook, right up to its logical extreme.
They fell right into the trap. Over and over again.
We aren’t done yet.
We haven’t even begun to see the beginning of the end of this yet.
The Twatter files are just a small taste of what’s to come.
There is lots more. Crimes against children. But before that, we haven’t seen The Twatter Q Files, where Trust and Safety totally went berserk internally trying like hair on fire to get the Q Army under control, where everything they did FAILED, always two steps behind 8kun.
It’s going to be beautiful.
And we were there folks, we were there on The Field of Fight, engaged in the front lines of an epic digital warfare for the ages.
The fewer the number the greater the share of the Glory, that’s what Henry V said.
👍
Spot on IMO.
“We few, we happy few. We band of brothers.”
And sisters!
Well, I use “brothers” in the wider sense, i.e. mankind.
Fair enough!
We know what you meant; we aren’t commies.
ROFL 😛
Yup. The Trust and Safety Q files will be very interesting.
YUP!!!
I see a bit of ‘Black pilling ‘ and despair here at the Q tree at times.
DON’T GIVE UP!!!
Unlike during the Tea Party days we now have, not only a BRILLIANT commanding officer but HE HAS a superb set of ‘high rank’ officers to help him.
We ARE WINNING battles. Yeah we lose some BUT we are winning the information war.
Look at Brazil. Lula can not rule WITHOUT acceptance by the population AND he does not have it. The DC Criminals tried to keep us from going that route by using the Jan 6th political prisoners to scare people.
More important the Q Team has kept us from going that route and instead directed us into the all important ‘Narrative War’ As the people on Badlands Media keep pointing out we are WINNING the narrative war.
The Kari Lake/Katie Hobbs Steal was a really BAD move. because it is SO BLATANT you have to be blind not to SEE how the corruption was done.
I actually think that might have been a clever trap. First you have a very pretty, savvy, sophisticated woman as the victim and then by BROADCASTING LOUDLY to vote on election day, the last day was a heavy Republican turn out. This was a surefire lure to the cheaters. We will see how that plays out because Kari Lake has NOT BEGUN TO FIGHT.
Oh and do not forget they tried to jail Gregg and Katherine during the critical time but were unable to.
Anyone ‘trusting’ the Biden/Hussein administration had to have a lot of screws loose.
Seriously. You have to either be in the tank for the Crims to trust them, or you have to be totally oblivious to the Crims’ obvious criminality.
People are literally better off to believe the exact opposite of anything the Crims say.
👍 Yes – agreed. Assume the opposite. Verify before trusting anything at all, and then question your own sanity for even thinking of trusting it.
Their original matrix required the media, ALL of it…not just big tech but news…Hollywood etc. to accomplish the brainwashing of enough of the normies to bolster the inevitability of their constructs. The CCP was comprehensive.
Thank you, Wolf and Gail, for your service to mankind.
Small story about how subtle and embedded it can all be right under our noses.
In our county, like across the country and around the world, college level Chinese females are granted student visas to attend local colleges. One of their “mentors” came to America in this manner a half dozen years ago and became a Christian. First off, I have no ability to judge her sincerity or to even question it. This is just an observation made over time.
She then married a backwoods Alabama boy who had moved to our area that she met at a Christian rally who wanted to find a job pastoring students in a local church while working a regular job and completing his online education through Liberty. After a series of come and go types, our local church hired him.
Soon afterwards, said Chinese wife went back to visit “family” in China for a couple of months, supposedly on a mission to spread the Christian message in that oppressed country. When she returned she began mentoring a new batch of about 10 college age Chinese women who had arrived with student visas to attend local colleges in the fall of 2019. She invited them to the church for a week where they participated in church classes, events, dinners, etc. and stayed in homes provided by the staff and congregation.
A few weeks later starting around Thanksgiving, a few members of our church began experiencing serious respiratory illnesses. Traditional prescriptions and treatments had little effect. More and more came down with it. A couple of members even had to leave a marriage retreat event as they became too ill to stay in early February. I am 99% certain that is when my wife and I first became infected with the same illness from contact with affected members at the event. And of course I am 99% certain it was the original Wuhan.
These Chinese women may be totally innocent. If they are, they are still being used and manipulated. If we could follow their progress, I am sure many will marry Americans or ship out for other countries to find spouses to embed into. I have my suspicions they are all embeds. The wife of the student pastor went on to have a child by him. Strangely enough, neither the wife or child attend church very often any more. The student pastor will eventually move on and take a church as senior pastor one day as he completes his studies. Knowing him as I do, I believe he is totally oblivious to what he may be assisting. Sort of a dull knife if you know what I mean.
Fascinating. And I will bet you’re right that something was going on. No matter what that gal’s personal thoughts may have been, she was almost certainly interviewed on returning to China, and from there, plans were made, with or without her consent. Her awareness, a continuum from unaware to fully, but likely in the low middle. Those student entries are typically by “trusted” individuals or family members. And that means trusted by CCP or PLA – not by us.
The fact that FIB allows CCP “police stations” in the United States – yeah. All part of WEF’s plan, IMO. Same with FIB police stations in Europe (see “FBI International”).
Makes me wonder what the CCP version of MK Ultra will ultimately look like.
Time to go back to watch the original 1962 version of The Manchurian Candidate for some background.
Yes. Watch THAT plus pay a lot of attention to McCain’s captivity by the North Vietnamese (who were brimming with Soviet and ChiCom psychologists and medical folks). He was badly injured with multiple fractures. Perfect subject.
I believe that McCain’s entire “honorable loss” and “bipartisan” nature was set by his captors. They likely used “5% down to 0%” pain, and “95% to 100%” reward. And the pain can be administered in a dissociated state, so that it is “forgotten” consciously, but remembered subconsciously, as motivation.
Didn’t McCain and David Kramer happen to be at the Aspen Institute at the same time as Glenn Simpson?
Yes, I seem to recall that. Aspen Institute is like a super-magnet for bad pennies!
Maurice Strong is where I first ran into the Aspen Institute. I have considered it a treasonous place ever since.
Yes! McCain was the perfect subject!
fib in Ukraine helping NABU in early Jan 2017 with Ciaramella and IG Michael Horowitz.
German Marshall Fund and Atlantic Council…Mr. Victoria Nuland, Robert Kagen. I think he is also connected to Brookings.
Nazis, Jazis, and WTFazis, assisted by FIBbies. What a world!
I agree.
Like them sending all those garment workers back into Italy and Europe in general after their annual pilgrimage back to China in January for their NY celebration. The people probably did not know they were infected, but they were obviously sent out to infect the world.
I’m going to quietly dig within the congregation, pastor and deacons to learn more about this.
Information about relations to CCP or the PLA will almost certainly have only been shared with people who were thought to be “safe” for not networking the information to suspicious cats. I found out about two high-level embedded officers long AFTER the fact, via a circuitous route, from people I normally didn’t interact with. Once I knew, thousands of circuits clicked.
I still remember that young Chinese woman in the car tag renewal line in late January 2020. She kept sidling up to me until I made it very very clear she was NOT to come near me. Realize I am an overweight gray haired lady and at the time I was wheezing thanks to Long Covid.
She must have thought I was the perfect subject to pass COVID to.
If ya posted a comment about that gal being to close, back in January 2020, I actually recall it. If it wasn’t you Gail, someone did a like post. 🙂
It was me. I was really angry.
One final comment. Our military has the ability to end this in 24 hours. The entire Chi-com empire can be vanquished systematically and quickly.
But the truth is they won’t be because of the people you discuss who are in league with them, remain in league with them doing the dirty.
Go look at the Fauci deposition. One very small example.
The new response to any reporting of public commentary by Fauci should remind his audience that he has no actual recollection of anything important related to his former job.
Damnesia!
FauXi’s no actual recollection is, almost as if by design, convenience to FauXi. /s
The CCP knows something I know, too:
Men are from Mars (god of War), Women are from Venus (goddess of Love).
So what did the enemy do, long term? They worked to ELEVATE American women, and to EMASCULATE American men. For decades.
All those women in the Twitter pic operate based on their FEELINGS. Not LOGIC. So they are easy to manipulate into anything, based on making them feel heroic and good.
I am a female, but as a Myers Briggs INTJ, I am also a unicorn. The rarest female personality type, I don’t operate on feelings but on logic.
Those “China-girls” that are sent over here have most likely been programmed FROM BIRTH to have a similar personality profile. If you start in the beginning, it’s not that hard to do. And you can weed out the ones that don’t take.
EXACTLY.
My wife is one of those ULTRA-RARE INTJ’s and she says the exact same thing.
Remember how White Suburban Liberal Women suffer from higher-than-normal rates of mental illness?
It’s EXACTLY like you say: They put EMOTIONAL (manipulation) ahead of logic (truth and objective reality).
Emotional people are highly subject to propaganda and ideological manipulation.
They always believe what they do is “right” and “for the greater good.” You could get them to do the most heinous of evil things if they think they are important (that they “matter”) and are doing it for a good cause (ending “oppression” for cosmic “justice” and the “arc of history”)
And yes, you have plenty of time from the beginning to see which ones take the best programming.
Keep in mind, too, that CCP exported this program for their recruitment
They use it extensively through infiltration in higher education – they try to manipulate, proselytize and convert people to the Woke Cult worldview.
Higher ed has been catering to women for decades. The stats are sobering – more women enroll and graduate in higher ed than men. Men’s enrollment is down. The radical leftist anti-human “feminists” celebrate this “decline of the patriarchy,” but really, that’s all just a code word for them celebrating the decline of civilization.
Men without trades are the definition of toxic masculinity.
Meanwhile, the women are heavily indoctrinated; unless they have a grounded foundation from their childhood, they’re easy pickings.
The women can become part of their army.
Those that don’t join the army directly are conscripted by other means.
The most obvious is the While Liberal Women Facebook Bubble: They are demographically manipulated by social media through advertising (everywhere you hear “advertising,” realize that means propaganda) toward a shrill narrow common demographic group. They share pictures of the kids and are fed a constant stream of outrage stories and emotional manipulation by the controlled algorithms.
It’s almost impossible to get away from Facebook in this Demo. It’s not cool anymore, but the school, the sports teams, the troops, and the churches are. Everybody uses Facebook (spit) as their primary means of communicating events and updates.
If you are a young married woman in the childbearing years, it’s nearly impossible to get away from the constant barraged psycho-emotional manipulation.
Bravo! And good for you, for nabbing a unicorn!
This part:
“Higher ed has been catering to women for decades. The stats are sobering – more women enroll and graduate in higher ed than men. Men’s enrollment is down. The radical leftist anti-human “feminists” celebrate this “decline of the patriarchy,” but really, that’s all just a code word for them celebrating the decline of civilization.”
I actually think this is GOOD news.
My son who went to college is ruined. My son who didn’t is thriving. Neither has much money, but college turned an Eagle Scout into a Marxist moron. And money isn’t everything.
That’s some sobering stuff right there!
It’s very depressing for me. I try not to dwell on it.
Sorry that you’re facing that challenge but take heart in the “train up a child” promise in scripture… “When he is Old he will not depart from ” the way he was taught as a child 🌹
I hope for that every day. Thank you.
YW Gotta bathe those “lost sheep” in prayer. Our Father is anxiously awaiting every prodigal’s return, I believe. God be with You & All of your family!
🙂
And consider that this information network is interconnected and positioned to not only diseminate and control information, but also to collect it across all platforms.
Think about that. Includes AirBnB and financial platforms.
Why do you think that they link data centers with industrial solar development?
Add in AI driven surveillance.
Amen!
Wolfie it is a multi-prong approach:
The women in the photo are Project Lighthouse in action. First AirBnB, then it was rolled out at Twitter, I’d guess.
https://www.theprojectlighthouse.org/team
So are they alums of the organization, schooled by it, or “allies”?
And who funds this project? It feels very “Soros”.
I think it reflects another company partnership like what was rolled out under Robinson while she was at AirBnB.
Gotcha. Send in the ringers, who become the bringers!
Gack.
WOW. That makes sense. Just like the East Germans “raising girls for the Olympics”.
Oh, yeah. And the Russian female swim team.
Your description nails my rock star wife as well.
She even uses her dad’s language and mannerisms when she talks. Cracks me up when she says, “Well, shitfire!” Being a hillbilly it comes out “sheetfar”.
Her favorite expression to me is to never trust a woman. Her ‘ Women are mean.” Me – “OK, but what about you, honey?” Her ‘ “I’m like my daddy, you can trust me.”
I’m afraid not to. 🤣
Lol! “Trust me.” 😉
LOL!!! SHEETFAR!
The subset problem. Child Porn allowed to thrive at Twitter long before Musk even thought of buying Twitter. Mary Morse wrote an extra piece about the infusion of FBI and other Intel types at Twitter that certainly belongs here. https://www.theqtree.com/2022/12/05/dear-kmag-20221205-joe-biden-didnt-win-%e2%9d%80-open-topic/comment-page-2/#comment-1004714
That was followed up by another observation and sure enough as we scout the internets others are seeing this subset problems as well. The below article is shown in it’s entirety being short enough and deserving enough to be part of this discussion.
The other enablers that should not be ignored?
 .
.
The established network allowed the algorithm to ignore the problem. It was focused elsewhere.
Convenient excuse for some, certainly not all. Meanwhile people who knew of the problem outside of Twitter didn’t need such an algorithm to know about their kiddie porn problem. Neither would of any of them, especially after folk began to report on it.
Kinda freaks me out that all those mother hen women running the mid-level show at Twitter were so oblivious *emotionally* to the kiddie porn. That’s a real distortion – but it matches all those female teachers who are now grooming students. That used to be unheard of. Now ridiculously common.
Exactly. “Trust and safety” focused on their boogie man – “white supremacy” and MAGA – while ignoring their allies with a high proportion of pedo.
Given that the [imported] engineers at Twitter didn’t realize that most MAGA were not “Russian bots”, it makes sense that they also didn’t realize a great truth of the internet.
Many “you would think they are white male” accounts are actually conservative blacks or women, who fly under ambiguity so that they can participate easily in the conversation without presumptions, and also so they can be “unladylike”. I discovered this on a particular site, getting to know the “usual accounts” over time. Sometimes the black accounts would spot each other and acknowledge in weak code. Even more often, women would decloak every once in a while. I can actually see a bit of that here, at the admin level, watching enough posts to learn who’s who, and the number of people who think the opposite.
Bottom line – many Twitter admins CAN ID the pedos, but took no action – likely so that the rotten elements of IC could leverage them IRL. Meanwhile, they did what SD called out the Obama administration for doing – turning the apparatus of “trust and safety” (meaning low-level intelligence) against WHAMs (white heterosexual American males).
And now I realize THAT truth. Trust and Safety is a method of growing CCP/WEF IC in America.
Epstein had a street victim recruitment model that we know of.
Where and how did Epstein intersect with the internet model of child exploitation?
Answering this could be quite revealing, imo.
MIT Media Lab, Harvard Kennedy School (home to the Belfer Center and Larry Summers)?
Just two of Epstein’s well connected known connections.
Epstein’s office/the space he funded was in a building owned by the Kennedy School iir. It’s in the final report of Harvard’s own investigation.
Wow.
Baker was a fellow at the Kennedy school in 2007.
https://hls.harvard.edu/faculty/james-a-baker/
Epstein was a Psych fellow in 2005-2006.
Via Kash Patel:
Kash on War Room: Everyone Needs to Focus on James Baker This Week
by: Kash Patel and Steve Bannon 12/05/2022 Source: Bannon`s War Room
https://fightwithkash.com/articles/kash-on-war-room-everyone-needs-to-focus-on-james-baker-this-week
Excellent. Sounds GREAT to me.
I’ll start. Let’s see where this goes, if anywhere:
1988 J.D. University of Michigan Law. Who else may have been there in ’88?
Hmmm…
Someone leaves DC law firm Caplin and Drysdale to join U.Michigan law faculty in 1987.
Becomes U.Mich law dean in 1994.
Next move, short term president of an ivy research institution, soon to be a 1000 talent.
Think Baker could be a student, 87-88? Anyone know anything about Caplin and Drysdale?
Hmmmm. This sounds interesting!
Fauci’s daughter worked for Twitter up until a year ago – ‘The plot thickens!’December 6, 2022 | Tom Tillison
https://www.bizpacreview.com/2022/12/06/faucis-daughter-worked-for-twitter-up-until-a-year-ago-the-plot-thickens-1314781/
OMG – is there “depop in the family”??? Bet she’s trusted with their plan.
OMG – that fits what Matt Taibbi reported! Censorship requests came in to a very large extent through individuals, who likely then dumped them into the internally known reporting mechanism!!!
Look into the Defending Digital Democracy Project. There are their own reports out there that identify the”stakeholders” that could flag problem accounts and the process that resulted in throttling. I posted links to this not long ago.
D3P links closely to Stanford. Home to the Freeman Spogli Center where Michael McFaul draws a paycheck, and recently hosted Zelinsky. Find links at previous posts.
Stanford is Condi Rice, William Browser, and Browser’s bott patenting son, Joshua.
https://profiles.stanford.edu/michael-mcfaul;jsessionid=79435C81749F9C86141A08AE5DE47018.cap-su-capappprd99
https://michaelmcfaul.com/photos/welcoming-ukrainian-president-volodymyr-zelensky
D3P is a Harvard Kennedy School’s Belfer Center sponsored project that partners with Stanford Internet Observatory.
https://www.belfercenter.org/project/defending-digital-democracy#!people
Alex Stamos (Facebook and Stanford)
Dimitry Alperovitch
Robby Mook
It’s a full circle to Russian attribution for the DNC “hack”.
Head of the Belfer Center D3P’s remarks to Senate SSCI:
…”Noting this, Facebook and Twitter must:
https://www.belfercenter.org/publication/defending-digital-democracy-four-corners-election-security
BOOM! OMG, this is massive. Straight out of Belfer. These toads absolutely have to be SEETHING at Musk right now.
He hasn’t shined a light on them yet.
Closest he gets is Twitter’s James Baker and Twitter’s Yoel Roth.
Hasn’t touched their network as yet, and his pockets aren’t deep enough to own the 15 platforms involved in the op, let alone their handlers, so far FBI, CIA, Atlantic Council/NATO, and Likely other agencies yet unnamed but represented by the 51 current and former Intel officials.
Just my theory and opinion…
Like McFaul, the Stanford Internet Observatory sits within the Freeman Spogli Institute. It was founded with a grant from the foundation of the guy that started Craigslist:
https://fsi.stanford.edu/news/stanford-internet-observatory-seeks-detect-internet-abuse-real-time
Seems to me that shutting down the New York Post classifies as “internet abuse”.
Seems to me that shutting down American and Brazilian voices is a “threat to democracy”.
These Belfer board commies are ORWELLIAN.
Sorry, not D3P, although they are involved.
EIP, Election Integrity Partnership. Here’s their final report:
https://purl.stanford.edu/tr171zs0069
See page 12 for the stakeholders that could issue tickets to flag accounts.
This is how they did it in their own words. 15 different social media platforms involved…
Link to EIP Executive Summary of the report:
https://www.eipartnership.net/report
A couple “Key Takeaways”:
…”Misleading and false claims and narratives coalesced into the metanarrative of a “stolen election,” which later propelled the January 6 insurrection.
…”The primary repeat spreaders of false and misleading narratives were verified, blue-check accounts belonging to partisan media outlets, social media influencers, and political figures, including President Trump and his family.
Remember that the social media op was lead by the FBI, according to CISA’s Matt Masterson, on the Atlantic Council Are We Ready…video. And Alicia Wanless of the Carnegie Endowment foreshadowed Jan. 6 in the same Aug. 2020 video, imo.
(This video is embedded above by Wolf.)
(This group focused on the election, apparently. Likely other groups focused on COVID and other topics.)
Interesting. After reading through my fellow QTree dwellers’ comments, this INFP is going to go in a different direction.
Most comments here are about STRATEGY.
I’m going to talk about TACTICS, specifically language that appeals to women and beta men.
SAFETY has been mentioned.
Protection
Wellness
Those are nurturing words. The language is being manipulated to get the softies to go along with the plans.
You see it in all aspects of life: healthcare, birth control, car seats, sunscreen, etc.
Note those are all motherly tasks and realms.
What other nurturing words are used for this purpose, and who thought up “misinformation” as part of this campaign.
Okay, that’s the Communications and Journalism major talking. Any time nurturing words are used in a campaign or strategy, BEWARE!
Excellent point! Oh, this makes so much sense!!! “BIG SISTER”.
Also note how by doing this, they replace actual family with “society as family”.
Don’t mother your own children. Mother the users.
This all fits in with a bigger picture.
“Experts” take the place of parents, etc.
Yes.
“Trusted authorities”!
Village elders!
It takes a communist village with “gatekeepers”!!!
Nanny state!
It takes a village, doncha know?
Yeah, it takes THEIR village.
Potemkin Village!
Son of a gun, yes!
We’re going to need a bigger FOIA
It’s one thing to release on the Twitter side, but we need digging on the .gov side to see who was requesting, what they were requesting, and what power they were being given or demanding.
CDC and Census Bureau had direct access to Twitter portal where they could flag speech for censorship
More Big Tech-Big Government censorship collusion.
By Tom Parker
https://reclaimthenet.org/cdc-census-bureau-twitter-portal-censorship/
Emails between an employee at the United States (US) Centers for Disease Control and Prevention (CDC) and Twitter have revealed that at least one CDC staff member and the US Census Bureau had access to Twitter’s dedicated “Partner Support Portal” which allows approved government partners to flag content to Twitter for censorship.
The emails were released by the nonprofit organization America First Legal and show Twitter enrolling a CDC employee into this portal through their personal account in May 2021 (pages 182-194).
On May 10, 2021, the CDC’s Carol Crawford sent Twitter employee Todd O’Boyle a list of example posts highlighting “two issues that we [the CDC] are seeing a great deal of misinfo about.” O’Boyle responded by saying that enrolling in Twitter’s Partner Support Portal is the best way for Crawford to get posts like this reviewed in the future.
. . .
Adding to the information:
𝗜 𝗱𝗼 𝗻𝗼𝘁 𝘁𝗵𝗶𝗻𝗸 ‘𝗦𝗲𝗰𝘂𝗿𝗶𝗻𝗴 𝗘𝗹𝗲𝗰𝘁𝗶𝗼𝗻𝘀’ 𝗠𝗘𝗔𝗡𝗦 𝘄𝗵𝗮𝘁 𝘄𝗲 𝘁𝗵𝗶𝗻𝗸 𝗶𝘁 𝗺𝗲𝗮𝗻𝘀.
From March 6, 2020 FBI’s Elvis Chan on Election Cybersecurity: Amidst Primary Elections, Focus is on Securing Democracy
[video src="https://c80211ea91bab460a01a-e73d423e7486dd5fc383150a57d2a8f5.ssl.cf1.rackcdn.com/RSAC2020-Elvis-Chan-1280x720.mp4" /]
INTERVIEWER: one of the foremost experts in Election security. … Within the FBI you are one of the go to people on elections. So what is the state of election security.
CHAN: SO there is no foreign interference in the Iowa Caucus… I would like to report that the FBI and the US Government as a whole is moving together in lock step getting ready for the big day.
INTERVIEWER: Describe how FBI has gotten ready (Paraphrased)
CHAN: Well there are a lot of different things that we are doing but I will limit it to a couple of things. I think on of the things that is really important to us that we did not have in 2016 WAS ESTABLISHED CHANNELS OF COMMUNICATION WITH PRIVATE SECTOR COMPANIES specifically SOCIAL MEDIA COMPANIES so we have done a much better job since 2016 of establishing channels of communication. Being able to SHARE THREAT INDICATORS WITH THEM SO THEY CAN PROTECT THEIR PLATFORM….. The other thing we have done, post 9/11, the interagency process of the intelligence community. We have been working really well on counter terrorism but maybe not quite as well on election security. So I can report we are doing a really good job …. Everyone is really well informed about what is happening right now and what is on the horizon…. [yeah LIKE THE MOST SECURE ELECTION CHANT FROM EVERYONE.]
The think I worry about is that people think their vote doesn’t count… [nNO SHIT DICK TRACY!]… There are a lot of things going on. There is a lot of things going on in the news there is a lot of first amendment free speech from American citizens, and everyone has a right to that if you are an American. THERE IS A LOT OF FOREIGN NOISE GOING ON and so I do not want the American People to get disheartened. At the end of the day you get to be informed do the research you need and then vote for the candidates you want … [Can I throwup now?] …
INTERVIEWER: How will you keep busy from now to election?
CHAN: Just so you know, with every FBI field office, what we have tried to do ahead of the election is to reach out to the county level registars right? THE FOLKS WHO ARE ACTUALLY IN CHARGE OF THE ELECTIONS FOR EACH STATE. AND I WOULD LIKE TO SAY WE ARE DOING A REALLY GOOD JOB OF THAT. We are not anticipating anything crasy to happen but better to have those channels of communication open ahead of time…. [Remember the guy in AZ saying he was THREATENED WITH PRISON IF HE DID NOT CERTIFY?] ….
INTERVIEWER: This must be an incredible experience for you.
Chan Absolutely. I AM USE TO WORKING RUSSIAN HACKERS …[Like the DNC hack?] ….We did the indictment of the FSB officers for the yahoo hack
[ASIDE TO ADD INFO]
March 15, 2017: U.S. Charges Russian FSB Officers and Their Criminal Conspirators for Hacking Yahoo and Millions of Email Accounts
A grand jury in the Northern District of California has indicted four defendants, including two officers of the Russian Federal Security Service (FSB), for computer hacking, economic espionage and other criminal offenses in connection with a conspiracy, beginning in January 2014, to access Yahoo’s network and the contents of webmail accounts.
[BACK TO THE INTERVIEW]
Little did I know the Russians would be you know would be working on the election stuff…. [ refuring to Russiagate according to Da Wolf] … It has been really FUN. Is FUN too strong a word? It has been really interesting and fun to work this and all the great people and ALL OF US HAVE THE SAME MISSION… [To get Trump out of office and a CCP puppet in?]
INTERVIEWER: Elvis our message goes out to hundreds, thousands of security leaders around the world particularly in the private sector. How can they be of assistance to you and your colleagues as you work to secure elections?
CHAN: As we at the FBI like to say, this is a whole of society approach. So what we need the private sector to do all the SISRs around is to keep banging the drum on cyber security because if we have resilient organizations whether public or private? That will help us in the long run.
INTERVIEWER: We Have Been Talking to Elvis Chan… For the Information Security Media Group.
Instead of trying to drag all the information over to this article I am going to post this pointer.
https://www.theqtree.com/2022/12/09/dear-maga-tgif-open-thread-20221209/
marymorse has a TON of good information like:
AND
[quote]
Reply to Sundance
Elon says no to Perkins Coie:
But Marc Elias was part of the Belfer Center D3P, a ticket issuing civil society stakeholder of the Stanford Election Integrity Partnership, and Twitter was a platform stakeholder.
[unquote]
PODESTA @ TWITTER
https://twitter.com/sourpatchlyds/status/1601285178412142592
https://twitchy.com/dougp-3137/2022/12/09/jack-dorsey-tried-to-fact-check-elon-musk-about-what-wasnt-a-crime-at-twitter-it-was-a-bad-idea/
Wonder if this girl has “shower diaries” as well.
Twitter’s “Trust and Safety Council,” formed in 2016, is officially dissolvedThe group behind an era of some of the most impactful political and cultural censorship is gone.
https://reclaimthenet.org/twitter-trust-and-safety-council-shut-down/
Twitter’s Trust and Safety Council is no more, an email sent to its members who remained after last week’s resignations reveals.
The email came on Monday, and now the about page for the former Council has also been removed.
On Friday, three members of the council resigned, citing disagreements with Elon Musk over the “safety and well-being” of Twitter users under his ownership.
Musk replied to a thread started by Anne Collier, one of the members who resigned from the now-dissolved body, by tweeting, “It is a crime that they [the Council] refused to take action on child exploitation for years!”