Ask yourself a simple question. Why should the very first examples of mRNA vaccines for humans violate the most important safety standard of the mRNA platform? Why would the vaccines do exactly what they PROMISED US the vaccines would not do?
TL;DR –
They didn’t just lie to us about the spike mRNA not going into the nucleus and not changing human DNA – the whole purpose was very likely to do exactly what they did – to open the cell nucleus and keep it open, so that we as a species can start changing population genomics in a huge way, using a variety of technologies.
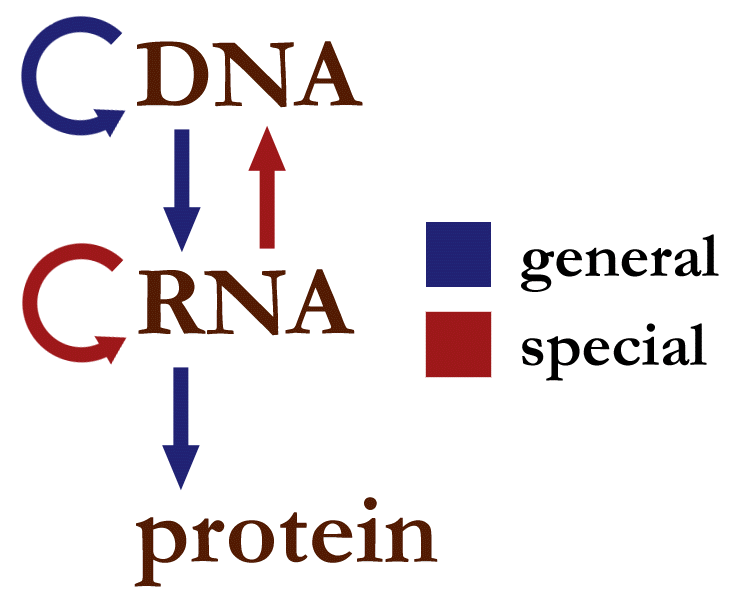
The central dogma of molecular biology. They shilled the blue arrows to the masses as lies about safety, while hiding the special red arrow and actually working to open it up for business.
Show-Time (Introduction)
I have finally realized that I need to spell out, in as many ways as needed, what is really going on with SARS-CoV-2 and these derived mRNA vaccines.
I had hoped that people would see the implications of the science which is now open to us, with the publication of first the Jaenish paper, then the De Marinis paper, and finally the Mehedi paper. I have commented extensively on each one of these papers, including very recently on the Mehedi paper, which really makes things obvious. I had thought that somebody more notable than me would try to make the point I am about to make. Sadly, nobody has, so it looks like I’m going to have to do it.
These vaccines are designed to BEGIN to change us on a fundamental level which is not exactly the same as the “transhumanism” that constitutes most of the “clickbait” against the vaccines. It’s similar, but it’s not the same. What we see in the clickbait is a distraction from the actual danger, which is not strange and distant and unbelievable, but is in fact right here, and right now, and very believable, once you understand it.
The truth is a lot more like GATTACA, and a lot less like Transcendence.


It’s already starting, and the infrastructure is being set up. The first step has actually been accomplished, and it was in many ways a HUGE success.
Humans ARE being engineered right in front of our eyes. I hope that you can see this point by the end of this article.
They (meaning WEF and its backers) hacked the human cell nucleus on a population genome level. They created a “Trojan” virus that appears to have “zero-dayed” the human cell nucleus. Artfully, the hack is a lot like state-level “APT” (advanced persistent threat) computer hacks, in that it gets in and holds the door open. Of course, better models can be created, but the self-replicating crowbar for the cell nucleus has obviously arrived, and its imperial version of SPQR is PRRARSV.
THAT is the fundamental advance that was achieved here.
I have to say, it was ingenious and “admirable”, in several senses – scientific, military, and criminal. Of course, your mileage may vary on “admirable”. Many will consider it “diabolical”.
What we are facing is the immediate REAL danger of biological engineering and eugenics, which was employed in a fantasy way, as a technical MacGuffin, in various episodes and productions in the Star Trek universe.

This is a scene from Star Trek II: The Wrath of Khan. These two people are “superhumans” who (according to the story) proved to be disastrous for Earth, during our current century (more or less). The one on the right is “Khan” – obviously in homage to Genghis Khan and his relatives, who ruled much of Asia for centuries.
Don’t get lost in the fantasy stuff. THAT is not the big danger. Stick around for an explanation of the reality which is actually upon us.
Here is how Wikipedia describes Khan, but more importantly, where he CAME FROM.
Khan Noonien Singh is a fictional character in the Star Trek science fiction franchise, who first appeared as the main antagonist in the Star Trek: The Original Series episode “Space Seed” (1967), and was portrayed by Ricardo Montalbán, who reprised his role in the 1982 film Star Trek II: The Wrath of Khan. In the 2013 film Star Trek Into Darkness, he is portrayed by Benedict Cumberbatch.
Khan had controlled more than a quarter of the Earth during the Eugenics Wars of the 1990s.[1] After being revived from suspended animation in 2267 by the crew of the Starship Enterprise, Khan attempts to capture the starship but is thwarted by James T. Kirk and exiled to Ceti Alpha V, where he has the chance to create a new society with his people. In Star Trek II: The Wrath of Khan, set fifteen years after “Space Seed”, Khan escapes his exile and sets out to exact revenge upon Kirk.
In Star Trek Into Darkness, set in the alternate continuity established in Star Trek (2009), Khan is awakened almost a decade before the events of “Space Seed“. Khan is given the false identity John Harrison and coerced by Admiral Marcus into building weapons for Section 31 and Starfleet in exchange for the lives of Khan’s crew. He ultimately rebels and comes into conflict with the crew of Enterprise.
OK – so what are the “Eugenics Wars”?
Back to Wikipedia…..
When the original series of Star Trek was produced, the 1990s were several decades away, and so various elements of the backstory to Star Trek are set in that era, particularly the Eugenics Wars. The references to the Eugenics Wars and to a nuclear war in the 21st century are somewhat contradictory.
The episode “Space Seed” establishes the Eugenics Wars, and has them lasting from 1992 to 1996. The Eugenics Wars are described as a global conflict in which the progeny of a human genetic engineering project, most notably Khan Noonien Singh, established themselves as supermen and attempted world domination. Spock calls them “the last of your so-called World Wars”, and McCoy identifies this with the Eugenics Wars.
OK – don’t get me wrong. I’m not saying it’s EXACTLY like Star Trek, although I do subscribe to the folk notion that Star Trek is a VERY good predictor of things that are likely to happen.
What I AM saying is that genetic engineering of humanity has already started, and now I’m going to explain why this is so.
We will take a brief tour into the PAST, before we return to the future. If a light bulb comes on, keep it lit!

Bonnie & Clyde of the Nucleus
BANKS make a really great analogy of the cell nucleus.
- they’re common and everywhere
- they contain valuable stuff that needs to be protected yet dispersed
- they have high security
- things need to traffic securely in and out of them
Breaking into a bank with very high security is a lot like what the spike protein does. But the spike protein doesn’t do it alone. THAT is an important point from the three papers I keep mentioning. The spike protein has a PARTNER who has all the plans.
OK – just for the record – this is going to deviate a little bit from the ACTUAL story of Bonnie and Clyde. Just warning you – it will get weird.
The spike protein and the spike protein mRNA are a PAIR, and together, they are able to not only break into the bank, but to totally take it over, and keep it taken over. And then to take over more banks.
Here is how it works.
The spike protein is Clyde. He’s got a gun, and he causes all kinds of trouble with it. He’s the “action” guy. He knows how to break into banks, mostly because he has a phony ID that always gets him in. The phony ID says PRRARSV in big letters on it, which makes all the bank guards at Cell Nucleus Bank and Trust say “Why, welcome, Mr. Barrow! We’re pleased to see you at the bank today! Come right on in!”
Or, to use a different analogy…..

These bank guards are such chumps, but it works every time.
Well, here is the problem for the bank. When Clyde goes in, he always brings his partner Bonnie. And SHE is trouble. She’s not so good with a gun or a fake ID, but she is a real scam artist, who knows how to get into the bank and embezzle the hell out of it.
Bonnie gets into the cell nucleus bank, and with some help from Clyde, she gets a permanent job there. Bonnie and Clyde are set for life. None of this “grab the cash, run out, get caught, and die in a hail of bullets” shit. No sir! THIS Bonnie and Clyde are smart.
Bonnie trains many of the new girls at the bank – and like the pod people in “Invasion of the Body Snatchers”, she turns every last one of them into exact copies of HERSELF. NASTY! So all these fresh Bonnies are trained by the bank and sent out to get into new banks.
But wait! Bonnie can’t get into banks. Bonnie doesn’t have a gun or a fake ID! How can she get into more banks?
Easy! Bonnie and all her Bonnie clones have the power of multiplication – not just to make more copies of each one herself, but to make more Clydes. Bonnie makes more copies of herself while she’s IN the bank, and she makes copies of Clyde while she’s OUT of the bank.
So every Bonnie that leaves the bank, creates hundreds of new Clydes on the outside. The next time Bonnie wanders near a bank, there are bound to be dozens of Clydes just hanging around, ready to escort her, and maybe even other gals [important], into the bank. If no Bonnie is already working there, she gets a job, and the process starts over.
The KEY POINT is that BONNIE makes the CLYDES who can get her, or women like her, into the next bank.
Bonnie can’t get into the bank, and Clyde can’t get a job in the bank, but together, they can make a living by embezzling banks.
Side Note: This is a beautiful example of a contradiction in the Marxist sense. Proteins and nucleic acids can’t do certain things alone, and thus NEED EACH OTHER.
Once Bonnie is on the payroll, this fact introduces a permanent security problem in the bank, and for all other banks.
And why is that?
Once Bonnie is on the payroll, you can’t get rid of her.
She will just create more Bonnies and more Clydes, and they will scam more banks.

In terms of banks, banks can resist just Clyde or just Bonnie, but they can’t resist the pair.
In terms of the cell nucleus, it can resist the spike protein or the spike mRNA, but it cannot resist both of them together.
Which pair, oddly, is exactly what the vaccines create.
WHAT ARE THE CHANCES?
We can use other analogies, using banks, which emphasize the spike protein more.
Imagine a bank that was convinced to crank out KEYS TO THE BANK, and to send out these keys. Imagine thousands of keys to the bank being sent out by the bank into the community, perhaps in a really stupid PR stunt.
God knows WHO is going to get into the bank now.
God knows WHAT is going to get into the genome now.
Are you starting to see what they did?
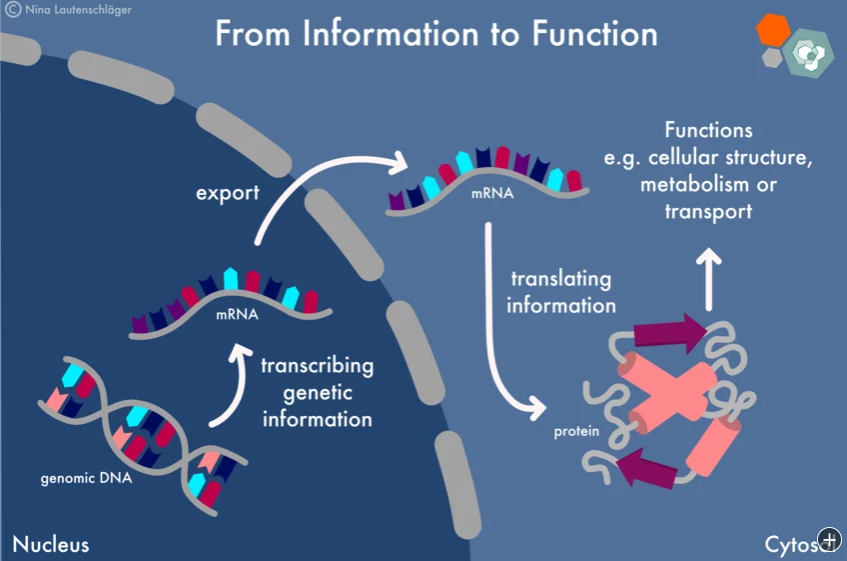
Fact Checking the Fact Checkers on DNA Change
The absolute best way for me to convince you that they really said these vaccines could not do what they are now proven to be doing, is to simply play back the words of the “fact checkers”.
See if you can spot how many LIES are told in this video.
If you’re not spotting the lies, read THIS ARTICLE.
AND – by the way – this video is a GREAT explanation of the way things NORMALLY work. It’s totally out to lunch on the way things ACTUALLY work.
Did you spot the lies? Tell me what you found in the comments.
This video is not alone – there are HUNDREDS OF THEM.
There are also hundreds if not thousands of articles of a similar nature. I’m just going to pick one of them – the one that happened to have the graphic I used above. That article is dated from MARCH of 2021 – right when the authorities were hard-selling the “vaccines”.
mRNA Covid-19 vaccines: Facts vs Fiction
MARCH 10, 2021
By: Maria Elisa Almeida Goes
Editing: Offspring Magazine Editorial Team
Images: Nina Lautenschläger.
LINK: https://www.phdnet.mpg.de/offspring/Covid-19_vaccines
ARCHIVE: https://archive.fo/irZec
Interestingly, this archive was made only 5 months ago. It was very likely archived by Wikipedia or somebody else who is shilling the false explanation, when faced with the emerging science showing nuclear translocation and genomic incorporation. But it’s perfect for me to preserve evidence.
As an aside, I find it terribly sad that this particular lover of “Max Planck” era scientific history, lived to see one of Planck’s namesake organizations lying about science on a grand scale, but yet here we are.
Let me just pull out the most relevant section. I was planning on highlighting ALL of the lies, fibs, evasions, etc., but there are so many, I decided to only highlight or [comment on] the most horrible and ironic.
mRNA vaccines will not alter your DNA, this is why:
Concerns about the effects mRNA vaccines over the integrity of our DNA also exist. Thankfully, you do not need to worry about this. Such an event would challenge everything scientists know about basic cell biology, and is so improbable, that one can actually call it impossible.
The main reason for that is that, besides being chemically and structurally different from DNA, mRNA is located in a different cellular compartment. While DNA is enclosed in the nucleus, mRNA is produced in the nucleus, but is quickly exported to the cytoplasm with a one-way ticket: it does not come back. In fact, only specific proteins carrying “nuclear localization signals” are able to migrate from the cytoplasm into the nucleus, and mRNA vaccines definitely do not include such molecular instruction. Thus, because mRNA cannot spontaneously be trafficked to the nucleus, it cannot modify your DNA sequence. Additionally, the RNA molecule is charged and carries the same charge as the nucleus, so as our 6th grade physics taught us, like charges repel, and hence the RNA molecule is physically repelled by the nucleus. [Note added by Wolf – WHAT THE HELL???]
One might also argue [HA! You TOADS! Yes, one “might”!] that there are mechanisms through which RNA can be integrated into the genome – HIV viruses being the classic example. The key differences here are that such viruses (1) express special enzymes which are able to code DNA back into RNA and (2) can associate with proteins that can traffic them into the nucleus. Neither scenario is applicable to the mRNA vaccines. [OH, THE IRONY]
For the same reasons, mRNA vaccines cannot affect your unborn children. This would require genomic mutations [oh, really!] in the reproductive cells – sperm and egg – since only these could potentially be transmitted to the next generation. [AND???!!!]
Speaking of children, you might have heard that Covid-19 vaccines would cause infertility in women [why don’t you just stop there, and not go on to one bad hypothesis?] because antibodies against the spike protein could mistakenly attack placenta cells, due to an alleged similarity with a placental protein called syncytin-1. There is no scientific evidence supporting this claim – and, in fact, the two proteins are barely similar, sharing only 4 sequential amino acids out of 538. [This did seem to be a bit of a miss. Nevertheless, what new hypothesis explains all the pregnancy problems?]
Still, you might want to ask why pregnant women are excluded from the vaccination campaigns [wait a minute….not in the US], and why, during clinical trials, women are asked to use contraceptive methods that will avoid pregnancy [because there might be a problem?]. Again, this is not a red flag. Any clinical trial for a potential vaccine or drug will exclude children, pregnant women, old people and people with specific underlying conditions. Initially, trials are designed to obtain major insights whether the developed pharmaceutical product works at all, in healthy adults. Once safety and efficacy are determined [read what you just said before that, where you excluded safety as a motive], tests are expanded to smaller groups that at first were set aside. Excluding pregnant women from trials only shows that trials are being done systematically and following standard protocols. [I’m sorry, but this sounds like happy horseshit, lady.]
Let’s concentrate on the lies most relevant to this discussion. I’ll isolate them and respond to each one.
In fact, only specific proteins carrying “nuclear localization signals” are able to migrate from the cytoplasm into the nucleus, and mRNA vaccines definitely do not include such molecular instruction.
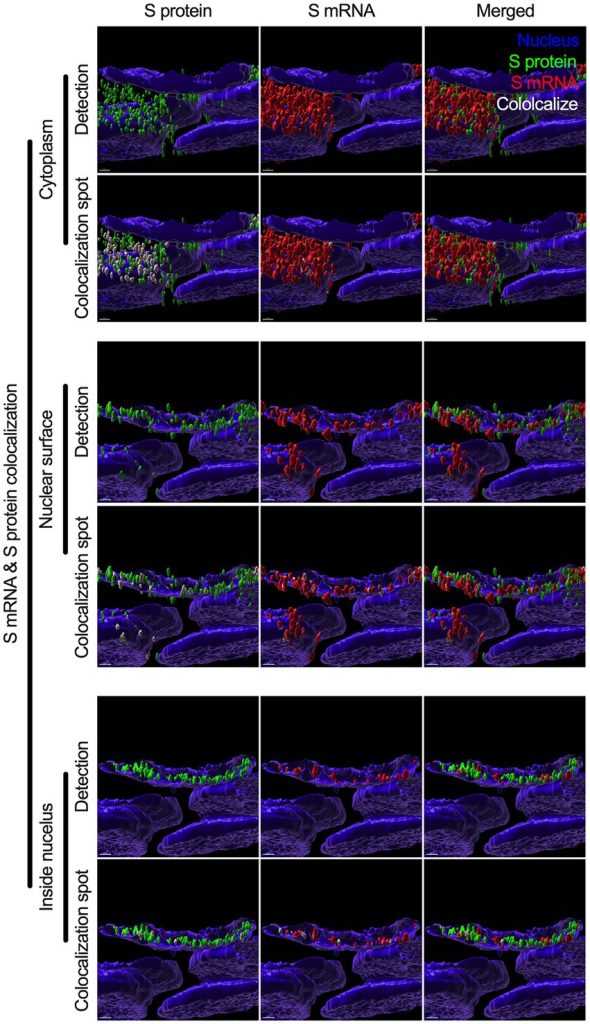
This is EXACTLY what was found with the spike protein that was produced by the full spike mRNA. What a coincidence! See De Marinis for proof that it happens, and Mehedi for WHY. OH – because there’s a nuclear location signal! Was it a “known” one, and if so, who knew it and who didn’t? If some people knew, and others didn’t, wouldn’t that make it like a “zero day” on the nucleus?
Thus, because mRNA cannot spontaneously be trafficked to the nucleus, it cannot modify your DNA sequence.
OH! But isn’t that SO STRANGE that the Mehedi work shows that the spike protein LITERALLY “traffics” the spike protein mRNA into the nucleus? WELL AHHHHH’LLLLL BE! So maybe this explains the nuclear DNA modification that is seen in the De Marinis results. Yes? Maybe? Come on, girl – you’re a scientist at a prestigious institute. Put on your big girl pants and hypothesize with me! You can do it! This is undergraduate, “smart-alec guy in the back of introductory class raises his hand” stuff! And when you were in that class, you thought the same sorts of things but didn’t raise your hand. Maybe it’s time to be brave!
One might also argue that there are mechanisms through which RNA can be integrated into the genome – HIV viruses being the classic example.
This should have been your really big hint, girl. Our local accountant named cthulhu realized that Fauci’s HIV interests and his bat virus interests had remarkable similarities, both in what he himself did, and in what he was studying. “This isn’t Fauci’s first rodeo.” Ask yourself – why was Fauci interested in this? Could it have been the same reason that Doudna was so interested in CRISPR-Cas9? The desire for WRITE PERMISSIONS on the genome?
The key differences here are that such viruses (1) express special enzymes which are able to code DNA back into RNA and (2) can associate with proteins that can traffic them into the nucleus. Neither scenario is applicable to the mRNA vaccines.
Thank you, my lying lady. You have just provided me with a huge clue, by the process of “liar subtraction” – a form of deductive reasoning. We know from De Marinis that genomic incorporation and modification is a fact. We know from Mehedi that “nuclear trafficking” (your point 2) is a fact. This means that it is almost certain that the spike protein ALSO acts as a promoter of reverse transcription (your point 1). You said it – not me. That sure seems convenient, doesn’t it? My question is now – DID YOU KNOW THIS? Were you part of the plot? Or was the person who reminded you of these things part of the plot? Or were we all part of the plot, when I, too, mindlessly parroted the “central dogma” as a defense of mRNA vaccines?
I’m willing to confess that I was wrong. I will admit to my part in promoting the conspiracy. Will you?
But their defenses get worse.
There are now MSM “fact checks” which specifically try to walk back the implications of both the Jaenisch and De Marinis papers, and you can bet there will be similar fact checks on Mehedi’s paper. There has likewise been pressure on those authors to DOWNPLAY the significance of their own works. To me, this is the height of bullshit.
Jaenisch Paper Downplay
Fact Check-Controversial MIT study does not show that mRNA vaccines alter DNA
LINK: https://www.reuters.com/article/factcheck-coronavirus-vaccines-idUSL1N2PK1DC
ARCHIVE: https://archive.fo/vJwBk
De Marinis Paper Downplay:
Swedish study on COVID vaccines and DNA misinterpreted
LINK: https://apnews.com/article/Fact-Check-COVID-Vaccine-Sweden-Study-986569377766
ARCHIVE: https://archive.fo/vJwBk
Rather than take these arguments apart myself, I ask you all to take a first crack at the different techniques used, by clicking the links and observing the UNETHICAL SKEPTICISM. Much of this does not require a science background.
In particular, knowing what we know now, after the Mehedi work, I think it should be very clear how much the media went to bat for the vaccines without honestly questioning the “authorities”.
I will confirm your findings in the comments, and catch any straggler sins of science.
To me, this media mendacity is all simple, stupid, and predictable.

“Nothing to see here!”
Frankly, it changes nothing for me, if any of these authors get talked into walking back their own work, because push-back on critical work is a common phenomenon in the history of science. Not all scientists are capable of weathering the storm. Here are TWO that did. Both got Nobel prizes, by the way.

A classic case, emphasizing a field aversion among an establishment group to a field solution emerging from deductive reasoning, was Van’t Hoff and tetrahedral carbon. Basically, a doctoral candidate in an applied science school had the temerity to take an old hypothesis and revive it as the solution to a very significant current problem. The guy was good – he went on to win a Nobel prize for other work. However, many chemists, especially older ones, rejected the idea, in my opinion by not prioritizing explanatory power over their own abstract philosophical preconceptions. The fact that important people rejected an elegant solution of remarkable utility and truth shows how bad group-think problems can be in science.

Another case was Rick Smalley and C60 (buckminsterfullerene). The linked article accurately describes the initial skepticism that people had for “soccer ball carbon” or “bucky balls”.
The Nature letter describing C60 was attractive and logical, but seeing a line in a mass spectrum did not convince all scientists of the discovery of a new allotrope of carbon. During the period 1985-1990, the Curl/Smalley team at Rice and Kroto at Sussex managed to amass a wide range of circumstantial evidence to support the fullerene structure proposal. Full acceptance came when Wolfgang Krätschmer of the Max Planck Institute for Nuclear Physics in Heidelberg, Germany, and Donald Huffman of the University of Arizona, with their students Konstantinos Fostiropoulos and Lowell Lamb, succeeded in synthesizing C60 in sufficient quantities to allow structural characterization.
I personally remember colleagues assuring me that Smalley was loony, demented, senile, past his prime, or at best something along the lines of “a nice guy, but clearly deluded and obsessed with an error.” The doubt about C60 as reality – particularly as a stable reality – ran thick. And that doubt was WRONG from the very beginning.
Scientists right now are NOT THINKING, and they’re letting the MEDIA push them around.
Scientists are also letting guys like Anthony FAUCI push them around, mainly by the horrible federal grant system, and by the psychology of woke universities, both designed to control science.
And that doesn’t even begin to address other malign interests altering science and medicine in dishonest ways.

Some Actual Speculation – Why Would They Push These Clearly Defective Shots So Hard?
You want some actual “conspiracy theorizing”? Here it is.
Let me go back to my “TLDR” again…..
They didn’t just lie to us about the spike mRNA not going into the nucleus and not changing human DNA – the whole purpose was very likely to do exactly what they did – to open the cell nucleus and keep it open, so that we as a species can start changing population genomics in a huge way, using a variety of technologies.
There are reasons to suspect depopulation as a motive for these vaccines, and both Gail Combs and I have written extensively about this. I continue to believe that this is part of the motivation of the “complex event” we have been undergoing, between virus and vaccine.
Depopulation is very important to these people.
MALTHUSIANS AND EUGENISTS MAKE A CASE FOR POPULATION CONTROL
DEPOPULATION – NEVER LET A CRISIS GO TO WASTE
The Population Control Shot – Introduction
The Population Control Shot – Understanding the Peoples Climate Temple
Likewise, there are many other motives, ranging from mercenary profits, to promoting gene therapy, to “Covid communism”, and beyond. Many of these roads lead back to WEF – the World Economic Forum. One of those roads may be an actual attempt to commit humanity to a future of genetic engineering as a kind of fait accompli.
Just listen to Yuval Noah Harari talk about changing humanity. A few times he talks about “we”, “I”, “me”, “my”, and “our” programs of genetic engineering of humanity. It’s not just creepy and megalomaniacal – it seems quite self-assured.
WEF’s interest in genetic transformation of humanity cannot be understated. You will note in the above video, the presence of Jennifer Doudna – the Nobel laureate who (IMO) was most responsible for pushing CRISPR gene editing technology forward. Here is the full video.
I have discussed the technology recently here:
Dear KMAG: 20230213 Joe Biden Didn’t Win ❀ Open Topic / Introduction to CRISPR/Cas9 Gene Editing Technology
This is a particularly good explanation for those who want to dig into the science a little.
So how does CRISPR-Cas9 connect to the spike protein?
I have mentioned that the spike not only is proven to have nucleus-opening properties and cell nuclear mRNA-trafficking properties, but it likely has reverse-transcribing properties as well. Thus, it may have utility in facilitating certain varieties of genomic incorporation of genetic material beyond its own spike mRNA. I’m leaving that open very broadly. We don’t really know how far the “nuclear translocation of mRNA” capabilities of the spike protein actually go.
But even just the incorporation of its own instructions into the cellular genome, makes the spike protein highly relevant to CRISPR-Cas9 gene editing technology.
We can’t REALLY be sure what happens if the spike protein code gets into egg or sperm DNA, and goes on to be a “feature” of every human cell of a “spike baby”, but I can say one thing – if that gene can be REMOVED during in vitro fertilization (IVF) by CRISPR-Cas9 technology, to the betterment of the child, then it’s very likely going to be demanded by elite parents, to assure a healthy baby.
So – I ask again – WHAT ARE THE CHANCES?
What are the chances, that people who are gung-ho on the “solution” of genetic modification of humanity – you know – like WEF – would have anything to do with releasing a virus and promoting a vaccine that would almost FORCE us into that future?
I think that this era is a lot like the chemical revolution of the late 1800s, precisely when Van ‘t Hoff was dealing with chemical theory. Figures like Malone and Doudna operate in the time of our own biological revolution. Remember Rockefeller, and what he did to science and medicine back during the chemical revolution. Well, now we have Gates and what HE did to science and medicine during the biological revolution.
Personally, I think it’s high time for us to stop taking shit from the corporate media – and particularly the “fact checkers” like Reuters and the AP – as they LIE to our faces about science – as they deny reality on behalf of the corporate titans behind them.
These mRNA vaccines are DEFECTIVE relative to how they were sold to us – very likely by intention – and the media and media organizations have LIED to us about those vaccines in the most scurrilous ways. The media has defended LIES and defrauded all of us.
You don’t have to be FOR or AGAINST gene editing per se, to be against LYING, DEFRAUDING, and FORCING IT ON THE WORLD by a criminal conspiracy.
We need to demand TRUTH about the vaccines, or the SHUTTERING of these “media” companies and organizations, which have cosigned onto crimes against humanity.
Demand no less. TRUTH or BREAK-UP. Media that lies and conceals is USELESS and a hindrance to REAL SCIENCE.
W